At ValidExamDumps, we consistently monitor updates to the TeraData TDVAN5 exam questions by TeraData. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the TeraData Vantage Administration Exam exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by TeraData in their TeraData TDVAN5 exam. These outdated questions lead to customers failing their TeraData Vantage Administration Exam exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the TeraData TDVAN5 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
What is a use case for Data Mover?
Teradata Data Mover is primarily designed to copy and replicate data between Teradata or Vantage systems. One of its common use cases is to move data to a disaster recovery system, ensuring that data is available in case of system failure or disaster, and making it a valuable tool for maintaining high availability and business continuity.
Archiving data to Hadoop and Copying data between Hadoop systems are more relevant to other tools such as Teradata QueryGrid, which integrates Vantage with Hadoop and other external systems.
Copying data between Vantage systems for active-active replication might involve Data Mover, but active-active replication typically involves more sophisticated real-time synchronization technologies like Teradata's Unity or QueryGrid.
The Administrator has received a request to add SELECT rights on the BusinessViews database to end users, developers, and batch accounts in the accounting unit. The following roles are set up for each group:
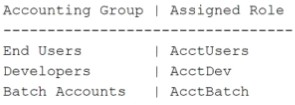
The Administrator created the AcctShared role and will use it in a role nesting strategy to provide the required access.
Which actions can the Administrator take to fulfill this request?
The AcctShared role should be granted SELECT access on the BusinessViews database. This ensures that the role itself has the necessary privileges.
Then, you can nest this role by granting AcctShared to the individual roles of AcctUsers, AcctDev, and AcctBatch. This role nesting strategy allows the users in these groups to inherit the permissions from AcctShared without having to directly grant the privileges to each individual role.
This approach maintains a clean and efficient permission structure using role nesting.
A system in Viewpoint is regularly reported as being in a critical state due to a lack of available AWT. No flow control is observed on the system. The Administrator identified that this is due to a recently completed cloud migration for the system that increased the number of available AWT from 80 to 120.
Which process task is required to set up the system in Viewpoint to address this problem?
After the cloud migration increased the number of available AWTs from 80 to 120, the thresholds for critical and degraded states in Viewpoint are likely still based on the old maximum of 80 AWTs. Since the system is now falsely reporting critical states due to this change, the thresholds need to be updated to reflect the new maximum of 120 AWTs. Increasing the degraded and critical thresholds by 40 (to account for the additional AWTs) will prevent unnecessary critical alerts.
An Administrator notices that a system appears to be near capacity and needs to get information about Input/Output Token Allocations (IOTA) for each workload.
How can this information be obtained?
The DBC.ResSpsView view provides resource usage information, including I/O-related metrics for workloads. It includes I/O Token Allocations (IOTA), which are essential for monitoring and managing system capacity.
The other options do not specifically provide I/O Token Allocation data:
DBC.ResSpmaView is used for monitoring memory allocations.
DBC.ResSpdskView focuses on disk space usage.
DBC.ResSldvView is related to logging device information.
Therefore, DBC.ResSpsView is the correct view to check for I/O Token Allocations.
The Administrator defined the following AWT resource limits in Viewpoint Workload Designer:
* Rule 1: A limit of 50 percent of AWTs for all DSA restore jobs in the system, with reject
* Rule 2: A limit of 20 percent of AWTs for DSA restore jobs from user UserA, with delay
* Rule 3: A limit of 10 percent of AWTs for DSA restore jobs from user UserB, with delay
UserB is running DSA restore jobs, consuming 10% of AWTs. Other users are running DSA restore jobs and consuming 40% of AWTs.
What will TASM do if UserA submits a DSA restore job request?
Rule 1 limits all DSA restore jobs in the system to 50% of AWTs. Currently, 40% of AWTs are consumed by other users, and UserB is consuming 10%. So, the total AWT usage is already at the 50% limit.
Since submitting a new DSA restore job from UserA would exceed the 50% limit set in Rule 1, TASM will delay the request, as Rule 1 applies system-wide.
Rule 2 applies specifically to UserA, but Rule 1 takes precedence since the total system AWT usage is already at the global 50% threshold.
Thus, TASM delays the job because it would violate the global AWT limit in Rule 1.