At ValidExamDumps, we consistently monitor updates to the SAP C_ABAPD_2309 exam questions by SAP. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the SAP Certified Associate - Back-End Developer - ABAP Cloud exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by SAP in their SAP C_ABAPD_2309 exam. These outdated questions lead to customers failing their SAP Certified Associate - Back-End Developer - ABAP Cloud exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the SAP C_ABAPD_2309 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Image:

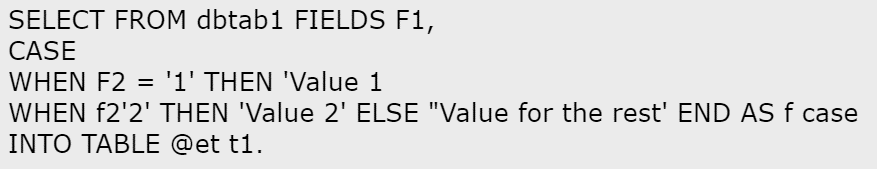
In the following ABAP SQL code, what are valid case distinctions? Note: There are 2 correct answers to this question.
A)
B)
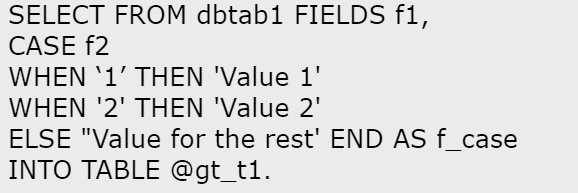
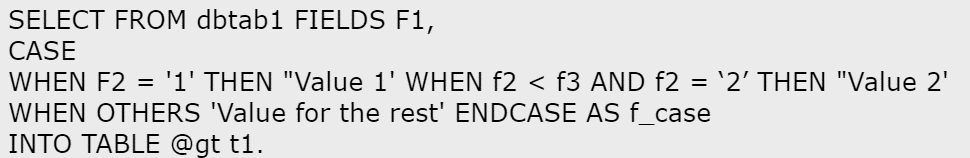
C)
D)
In a test method you call method cl_abap_unit_assert=>assert_equals( .. ) in the following way:
CLASS Itcl1 DEFINITION FOR TESTING RISK LEVEL HARMLESS DURATION SHORT.
PRIVATE SECTION.
METHODS m1 FOR TESTING.
ENDCLASS.
CLASS Itcl1 IMPLEMENTATION.
METHOD m1.
DATA: go_test_object TYPE REF TO zcl_to_be_tested.
CONSTANTS: Ico_exp TYPE string VALUE 'test2'.
CREATE OBJECT go_test_object.
cl_abap_unit_assert=>assert_equals(
EXPORTING
act = go_class->mv_attribute
exp = lco_exp
msg = 'assert equals failed ' && go_test_object->mv_attribute && ' ' && lco_exp
ENDMETHOD.
ENDCLASS.
What will happen if method parameters act and exp are not equal?
Exhibit:
With Icl_super being superclass for Icl_subl and Icl_sub2 and with methods subl_methl and sub2_methl being subclass-specific methods of Id_subl or Icl_sub2, respectivel. What will happen when executing these casts? Note:
There are 2 correct answers to this question
The following are the explanations for each statement:
Which of the following ABAP SQL statements are valid? Note: There are 2 correct answers to this question.
The following are the explanations for each ABAP SQL statement:
A: This statement is valid. It selects the fields carrid, airpfrom, and the aggregate functions MAX(distance) and MIN(distance) from the table /dmo/connection, and groups the results by carrid and airpfrom. The aggregate functions are aliased as dist_max and dist_min. The results are stored in an internal table named It_hits, which is created using the inline declaration operator @DATA.
B: This statement is valid. It is similar to statement A, except that it does not specify the GROUP BY clause. This means that the aggregate functions are applied to the entire table, and the results are stored in an internal table named It_hits, which is created using the inline declaration operator @DATA.
C: This statement is invalid. It selects the aggregate functions MAX(distance) and MIN(distance) from the table /dmo/connection, but it does not specify any grouping or non-aggregate fields. This is not allowed in ABAP SQL, as the SELECT list must contain at least one non-aggregate field or a GROUP BY clause. The statement will cause a syntax error.
D: This statement is invalid. It selects the fields carrid and airpfrom from the table /dmo/connection, and groups the results by carrid and connid. However, the field connid is not included in the SELECT list, which is not allowed in ABAP SQL, as the GROUP BY clause must contain only fields that are also in the SELECT list. The statement will cause a syntax error.
You are given the following information:
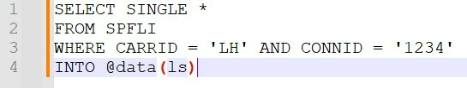
1.
The data source "spfli" on line #2 is an SAP HANA
database table
2.
"spfli" will be a large table with over one million rows.
3.
This program is the only one in the system that accesses
the table.
4.
This program will run rarely.
Based on this information, which of the following general
settings should you set for the spfli database table? Note:
There are 2 correct answers to this question.
Based on the given information, the spfli database table should have the following general settings: