At ValidExamDumps, we consistently monitor updates to the Palo Alto Networks PCNSE exam questions by Palo Alto Networks. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Palo Alto Networks Certified Security Engineer PAN-OS 11.0 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Palo Alto Networks in their Palo Alto Networks PCNSE exam. These outdated questions lead to customers failing their Palo Alto Networks Certified Security Engineer PAN-OS 11.0 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Palo Alto Networks PCNSE exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
An administrator plans to install the Windows User-ID agent on a domain member system.
What is a best practice for choosing where to install the User-ID agent?
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClhwCAC
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-networking-admin/nat/source-nat-and-destination-nat/source-nat
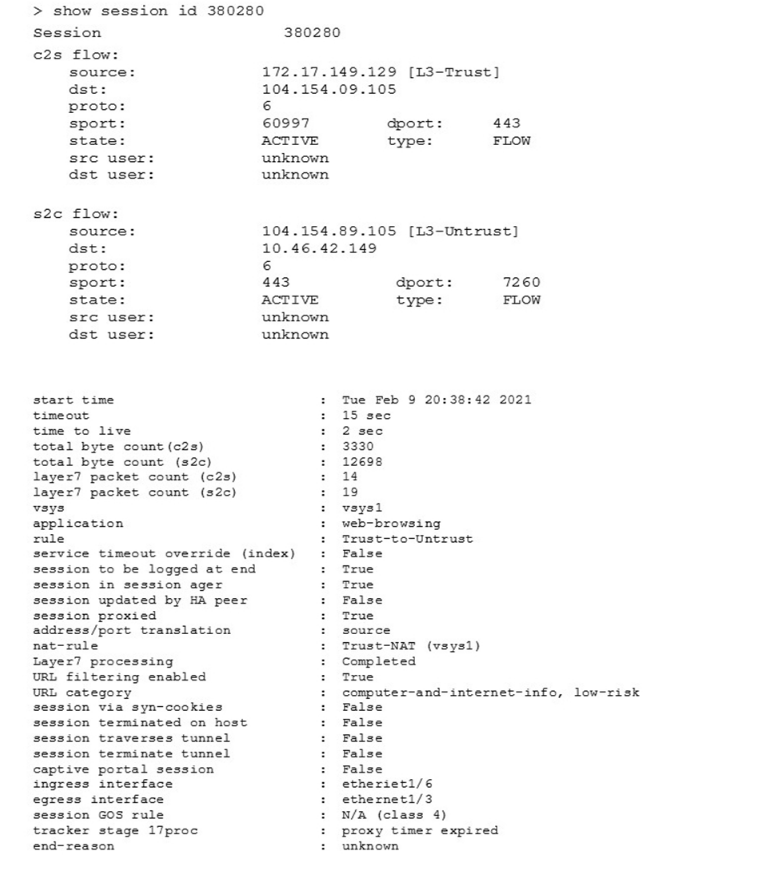
Which two statements correctly describe Session 380280? (Choose two.)
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is currently processing traffic?
A standalone firewall with local objects and policies needs to be migrated into Panoram
a. What procedure should you use so Panorama is fully managing the firewall?