At ValidExamDumps, we consistently monitor updates to the Palo Alto Networks PCDRA exam questions by Palo Alto Networks. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Palo Alto Networks Certified Detection and Remediation Analyst exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Palo Alto Networks in their Palo Alto Networks PCDRA exam. These outdated questions lead to customers failing their Palo Alto Networks Certified Detection and Remediation Analyst exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Palo Alto Networks PCDRA exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Cortex XDR Analytics can alert when detecting activity matching the following MITRE ATT&CKTM techniques.
Under which conditions is Local Analysis evoked to evaluate a file before the file is allowed to run?
Local Analysis is a feature of Cortex XDR that allows the agent to evaluate files locally on the endpoint, without sending them to WildFire for analysis. Local Analysis is evoked when the following conditions are met:
The endpoint isdisconnectedfrom the internet or the Cortex XDR management console, and therefore cannot communicate with WildFire.
The verdict from WildFire is of a typeunknown, meaning that WildFire has not yet analyzed the file or has not reached a conclusive verdict.
Local Analysis uses machine learning models to assess the behavior and characteristics of the file and assign it a verdict of either benign, malware, or grayware. If the verdict is malware or grayware, the agent will block the file from running and report it to the Cortex XDR management console. If the verdict is benign, the agent will allow the file to run and report it to the Cortex XDR management console.Reference:
Local Analysis
WildFire File Verdicts
What is the action taken out by Managed Threat Hunting team for Zero Day Exploits?
The Managed Threat Hunting (MTH) team is a group of security experts who proactively hunt for threats in the Cortex XDR tenant and generate a report with the findings. The MTH team uses advanced queries and investigative actions to identify and analyze potential threats, such as zero-day exploits, that may have bypassed the prevention and detection capabilities of Cortex XDR. The MTH team also provides recommendations and best practices to help customers remediate the threats and improve their security posture.Reference:
Managed Threat Hunting Service
Which statement is true based on the following Agent Auto Upgrade widget?
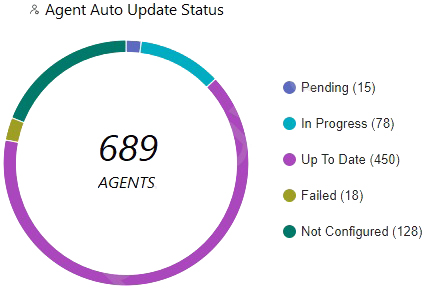
The Agent Auto Upgrade widget shows the status of the agent auto upgrade feature on the endpoints. The widget displays the number of agents that are up to date, in progress, pending, failed, and not configured. In this case, the widget shows that there are 450 agents that are up to date, 78 in progress, 15 pending, 18 failed, and 128 not configured. This means that the agent auto upgrade feature was enabled but not on all endpoints.Reference:
Cortex XDR Agent Auto Upgrade
PCDRA Study Guide
Which statement regarding scripts in Cortex XDR is true?
The correct answer is B, the level of risk is assigned to the script upon import. When you import a script to the Agent Script Library in Cortex XDR, you need to specify the level of risk associated with the script. The level of risk determines the permissions and restrictions for running the script on endpoints. The levels of risk are:
Low: The script can be run on any endpoint without requiring approval from the Cortex XDR administrator. The script can also be used in remediation suggestions or automation actions.
Medium: The script can be run on any endpoint, but requires approval from the Cortex XDR administrator. The script can also be used in remediation suggestions or automation actions.
High: The script can only be run on isolated endpoints, and requires approval from the Cortex XDR administrator. The script cannot be used in remediation suggestions or automation actions.
The other options are incorrect for the following reasons:
A is incorrect because not any version of Python script can be run in Cortex XDR. The scripts must be written in Python 2.7, and must follow the guidelines and limitations described in the Cortex XDR documentation. For example, the scripts must not exceed 64 KB in size, must not use external libraries or modules, and must not contain malicious or harmful code.
C is incorrect because not any script can be imported to Cortex XDR, including Visual Basic (VB) scripts. The scripts must be written in Python 2.7, and must follow the guidelines and limitations described in the Cortex XDR documentation. VB scripts are not supported by Cortex XDR, and will not run on the endpoints.
D is incorrect because the script is not run on the machine uploading the script to ensure that it is operational. The script is only validated for syntax errors and size limitations when it is imported to the Agent Script Library. The script is not executed or tested on the machine uploading the script, and the script may still fail or cause errors when it is run on the endpoints.
Import a Script