At ValidExamDumps, we consistently monitor updates to the Netskope NSK300 exam questions by Netskope. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Netskope Certified Cloud Security Architect exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Netskope in their Netskope NSK300 exam. These outdated questions lead to customers failing their Netskope Certified Cloud Security Architect exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Netskope NSK300 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Review the exhibit.
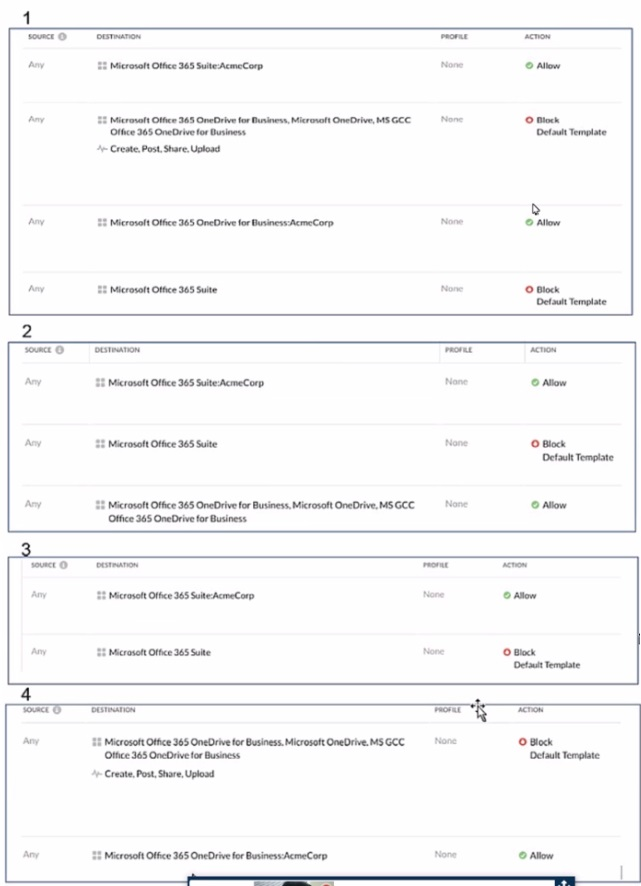
AcmeCorp has recently begun using Microsoft 365. The organization is concerned that employees will start using third-party non-AcmeCorp OneDrive instances to store company dat
a. The CISO asks you to use Netskope to create a policy that ensures that no data is being uploaded to non-AcmeCorp instances of OneDrive.
Referring to the exhibit, which two policies would accomplish this posture? (Choose two.)
To ensure that no data is uploaded to non-AcmeCorp instances of OneDrive, the policies that would accomplish this are:
Policy B: This policy allows traffic only for AcmeCorp's OneDrive and blocks all other Microsoft 365 Suite traffic. It ensures that data is not uploaded to non-AcmeCorp OneDrive instances by restricting access to only the corporate instance of OneDrive.
Policy C: This policy allows traffic for AcmeCorp's Microsoft 365 Suite but blocks all other OneDrive for Business traffic. It achieves the same outcome by permitting corporate suite usage while preventing uploads to any OneDrive for Business instances that are not part of AcmeCorp.
These policies are designed to provide granular control over the data flow, ensuring that company data remains within the corporate environment and is not transferred to external or personal storage solutions.
You recently began deploying Netskope at your company. You are steering all traffic, but you discover that the Real-time Protection policies you created to protect Microsoft OneDrive are not being enforced.
Which default setting in the Ul would you change to solve this problem?
When deploying Netskope and steering all traffic, if you find that the Real-time Protection policies for Microsoft OneDrive are not being enforced, the likely issue is with the default steering exceptions. To resolve this, you shouldremove the default steering exception for domains . This is because the default exceptions may include domains related to Microsoft services, which could prevent the Real-time Protection policies from being applied to traffic directed towards OneDrive. By removing these exceptions, you ensure that all traffic, including that to OneDrive, is subject to the policies you have set up.
You are currently designing a policy for AWS S3 bucket scans with a custom DLP profile Which policy action(s) are available for this policy?
You deployed Netskope Cloud Security Posture Management (CSPM) using pre-defined benchmark rules to monitor your cloud posture in AWS, Azure, and GCP. You are asked to assess if you can extend the Netskope CSPM solution by creating custom rules for each environment.
Which statement is correct?
Netskope Cloud Security Posture Management (CSPM) allows for the creation of custom rules using Domain Specific Language (DSL) for all three major cloud platforms: AWS, Azure, and GCP. This capability is integral to CSPM and enables organizations to tailor their security posture assessments to their specific needs across different cloud environments.
Your CISO asks that you to provide a report with a visual representation of the top 10 applications (by number of objects) and their risk score. As the administrator, you decide to use a Sankey visualization in Advanced Analytics to represent the data in an efficient manner.
In this scenario, which two field types are required to produce a Sankey Tile in your report? {Choose two.)


To produce a Sankey Tile in a report that visually represents the top 10 applications by number of objects and their risk score, you would need:
These two field types are essential for creating a Sankey visualization as they define the structure and flow of data between different stages or categories within the visualization.