At ValidExamDumps, we consistently monitor updates to the Netskope NSK200 exam questions by Netskope. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Netskope Certified Cloud Security Integrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Netskope in their Netskope NSK200 exam. These outdated questions lead to customers failing their Netskope Certified Cloud Security Integrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Netskope NSK200 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You are integrating Netskope tenant administration with an external identity provider. You need to implement role-based access control. Which two statements are true about this scenario? (Choose two.)
Review the exhibit.
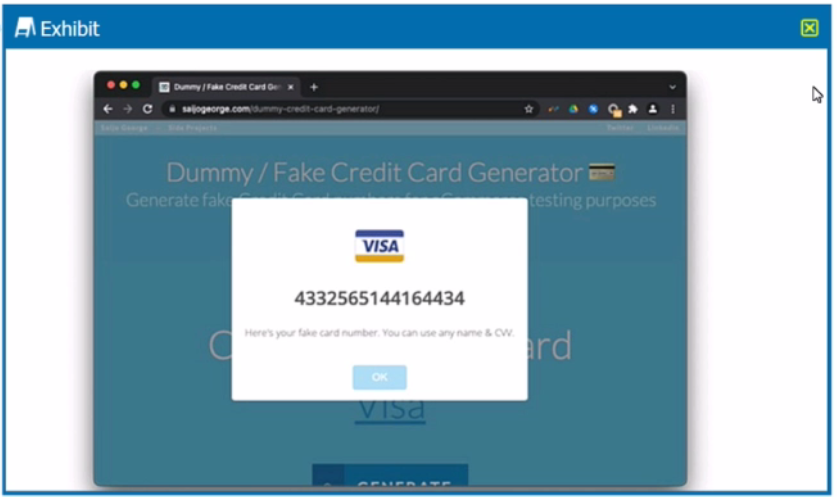
You are asked to create a DLP profile that will ensure that the data shown in the exhibit cannot be uploaded to a user's personal Google Drive.
What must be used to accomplish this task?
Review the exhibit.
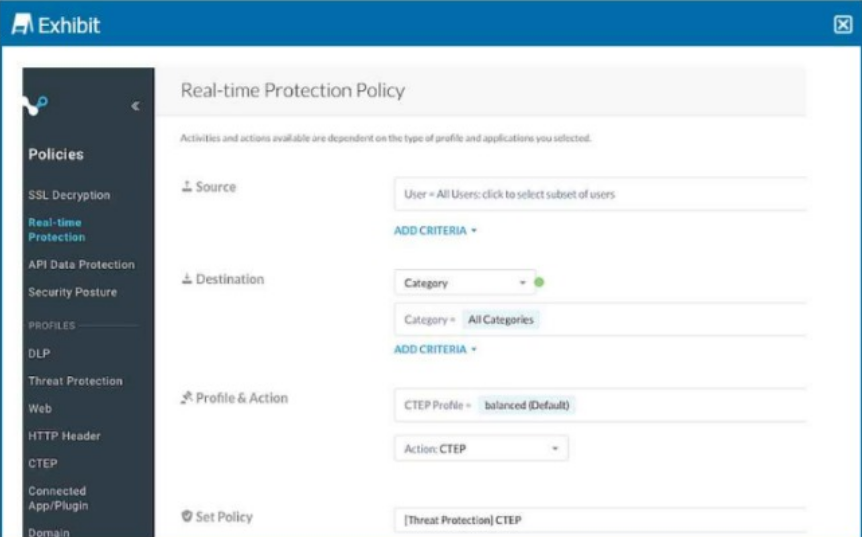
Your Real-time Protection policy contains some rules with only a browse activity. The exhibit shows a new policy rule.
Where is the correct location to place this rule?
The correct practice is to place high-priority rules, such as those with specific scanning actions, at the top of the Real-time Protection policy rule list. Placing the rule at the top ensures it is applied before other less restrictive rules, like those configured only for browsing activities.
Review the exhibit.
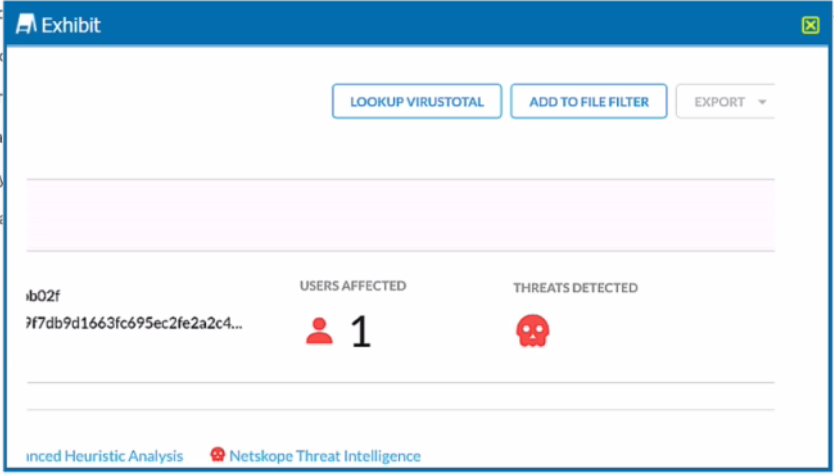
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your security team has confirmed that the virus was a test data file You want to allow the security team to use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
To allow the security team to use the test data file that was detected as a virus by the Netskope Heuristics Engine, the following two steps are correct:
https://docs.netskope.com/en/netskope-help/admin-console/incidents/
A city uses many types of forms, including permit applications. These forms contain personal and financial information of citizens. Remote employees download these forms and work directly with the citizens to complete them. The city wants to be able to identify and monitor the specific forms and block the employees from downloading completed forms.
Which feature would you use to accomplish this task?