At ValidExamDumps, we consistently monitor updates to the Microsoft SC-401 exam questions by Microsoft. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Microsoft Administering Information Security in Microsoft 365 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Microsoft in their Microsoft SC-401 exam. These outdated questions lead to customers failing their Microsoft Administering Information Security in Microsoft 365 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Microsoft SC-401 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You have a Microsoft 565 subscription that contains 100 users and a Microsoft 365 group named Group1. All users have Windows 11 devices and use Microsoft SharePoint Online and Exchange Online. A sensitivity label named Label! is published as the default label for Group1. You add two sublabels named Sublabel1 and Sublabel2 lo Label1. You need to ensure that the settings in Sublabel 1 are applied by default to Group 1. What should you do?
You have a Microsoft 365 E5 subscription. The subscription contains 500 devices that are onboarded to Microsoft Purview.
You select Activate Microsoft Purview Audit.
You need to ensure that you can track interactions between users and generative AI websites.
What should you deploy to the devices?
To track interactions between users and generative AI websites in Microsoft Purview Audit, you need to deploy the Microsoft Purview browser extension to the devices. This extension enables tracking of user activities on web-based applications, including AI-related tools like ChatGPT, Microsoft Copilot, and other generative AI platforms.
Microsoft Purview extension provides visibility into browser-based activities, including AI tool usage, ensuring compliance and risk management within Microsoft Purview. This extension works with Microsoft Edge and Google Chrome to track and log user interactions.
You have a Microsoft 365 subscription that contains the devices shown in the following table.
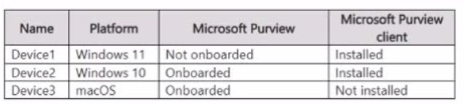
From which devices can Microsoft Purview Insider Risk Management capture forensic evidence?
You have a Microsoft 365 E5 subscription.
You plan to implement insider risk management for users that manage sensitive data associated with a project.
You need to create a protection policy for the users. The solution must meet the following requirements:
Minimize the impact on users who are NOT part of the project.
Minimize administrative effort.
What should you do first?
To implement insider risk management for users managing sensitive project data while minimizing the impact on other users and reducing administrative effort, you should first create a security group in Microsoft Entra ID (formerly Azure AD).
Security groups allow you to scope insider risk management policies to specific users instead of applying policies to all users, which helps in minimizing unnecessary alerts and reducing administrative overhead. After creating the security group, you can assign this group to a Microsoft Purview Insider Risk Management policy, ensuring that only project-related users are affected.
You have a Microsoft 365 E5 subscription that uses retention label policies.
You need to identify all the changes made to retention labels during the last 30 days.
What should you use in the Microsoft Purview portal?