At ValidExamDumps, we consistently monitor updates to the Microsoft SC-400 exam questions by Microsoft. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Microsoft Information Protection Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Microsoft in their Microsoft SC-400 exam. These outdated questions lead to customers failing their Microsoft Information Protection Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Microsoft SC-400 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You have a Microsoft 365 subscription that uses Microsoft Exchange Online.
You need to receive an alert if a user emails sensitive documents to specific external domains.
What should you create?
You have a Microsoft 365 subscription that contains the users shown in the following table.
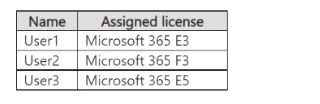
You review the audit retention period of each user. Which users' audit logs are retained for nine months?
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
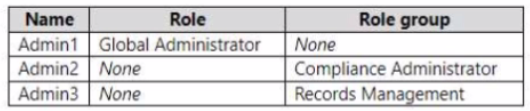
You create the retention label shown in the following exhibit.
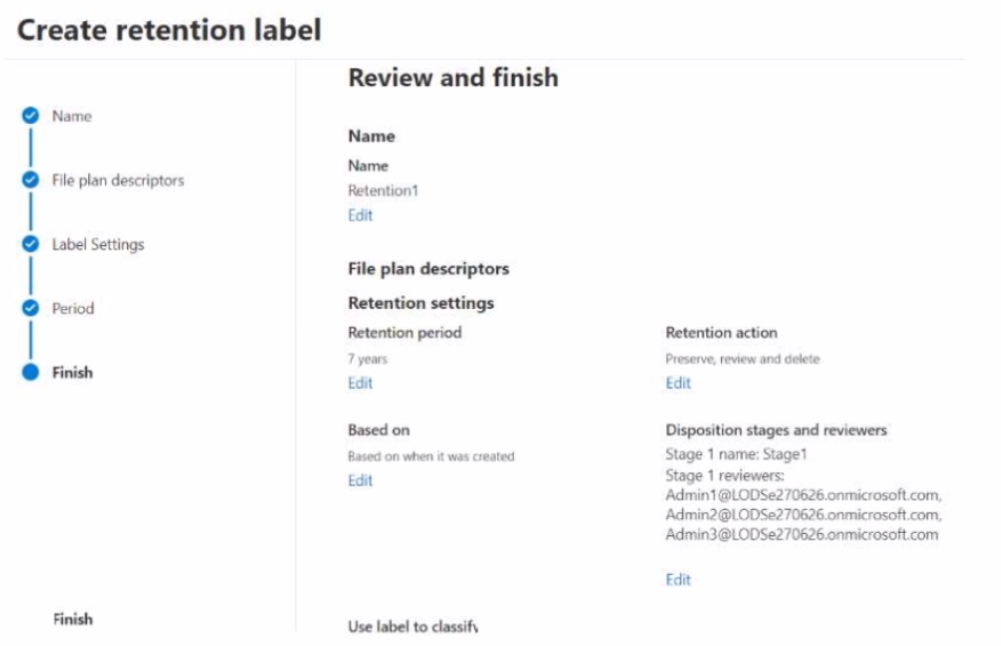
Which users can perform a disposition review of content that has Retention 1 applied?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Build-in DLP inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
You have a Microsoft 365 E5 subscription.
You create a role group named Rote1.
You need to add a role to Role1 that will enable group members to view the metadata of records that were tagged for deletion automatically at the end of the records' retention period. The solution must use the principle of least privilege.
Which role should you add?