At ValidExamDumps, we consistently monitor updates to the Linux Foundation CKS exam questions by Linux Foundation. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Linux Foundation Certified Kubernetes Security Specialist exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Linux Foundation in their Linux Foundation CKS exam. These outdated questions lead to customers failing their Linux Foundation Certified Kubernetes Security Specialist exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Linux Foundation CKS exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Context
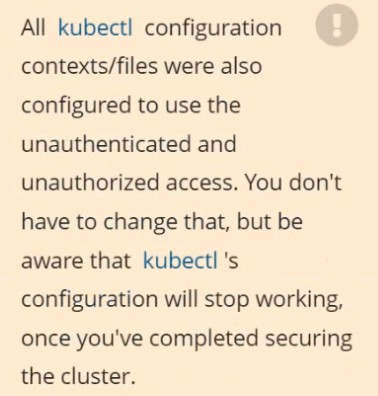
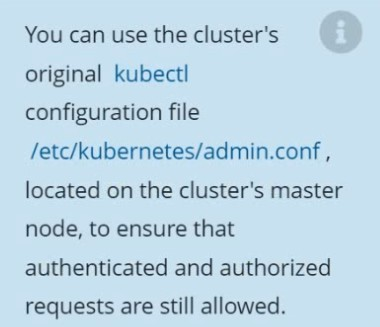
The kubeadm-created cluster's Kubernetes API server was, for testing purposes, temporarily configured to allow unauthenticated and unauthorized access granting the anonymous user duster-admin access.
Task
Reconfigure the cluster's Kubernetes API server to ensure that only authenticated and authorized REST requests are allowed.
Use authorization mode Node,RBAC and admission controller NodeRestriction.
Cleaning up, remove the ClusterRoleBinding for user system:anonymous.
Two tools are pre-installed on the cluster's worker node:
Using the tool of your choice (including any non pre-installed tool), analyze the container's behavior for at least 30 seconds, using filters that detect newly spawning and executing processes.
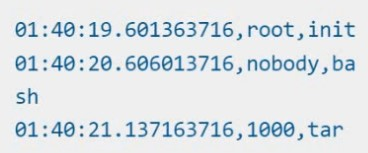
Store an incident file at /opt/KSRS00101/alerts/details, containing the detected incidents, one per line, in the following format:

The following example shows a properly formatted incident file:

Cluster:qa-cluster Master node:masterWorker node:worker1 You can switch the cluster/configuration context using the following command: [desk@cli] $kubectl config use-context qa-cluster Task: Create a NetworkPolicy namedrestricted-policyto restrict access to Podproductrunning in namespacedev. Only allow the following Pods to connect to Pod products-service: 1. Pods in the namespaceqa 2. Pods with labelenvironment: stage, in any namespace
Cluster:scanner Master node:controlplane Worker node:worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $kubectl config use-context scanner
Given: You may use Trivy's documentation.
Task: Use the Trivy open-source container scanner to detect images with severe vulnerabilities used by Pods in the namespacenato.
Look for images withHighorCriticalseverity vulnerabilities and delete the Pods that use those images. Trivy is pre-installed on the cluster's master node. Use cluster's master node to use Trivy.
On the Cluster worker node, enforce the prepared AppArmor profile
#include
profile nginx-deny flags=(attach_disconnected) {
#include
file,
# Deny all file writes.
deny /** w,
}
EOF'
Edit the prepared manifest file to include the AppArmor profile.
apiVersion: v1
kind: Pod
metadata:
name: apparmor-pod
spec:
containers:
- name: apparmor-pod
image: nginx
Finally, apply the manifests files and create the Pod specified on it.
Verify: Try to make a file inside the directory which is restricted.