At ValidExamDumps, we consistently monitor updates to the Huawei H12-722 exam questions by Huawei. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Huawei HCIP-Security-CSSN V3.0 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Huawei in their Huawei H12-722 exam. These outdated questions lead to customers failing their Huawei HCIP-Security-CSSN V3.0 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Huawei H12-722 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Regarding the enhanced mode in HTTP Flood source authentication, which of the following descriptions are correct? Multiple choices
When configuring the URL filtering configuration file, www.bt.com is configured in the URL blacklist-item: At the same time, set it in the custom URL category.
A URL is set as bt.com, and the action of customizing URL classification is a warning. Regarding the above configuration, which of the following statements are correct? (More
select)
The following figure is a schematic diagram of the detection file of the firewall and the sandbox system linkage.
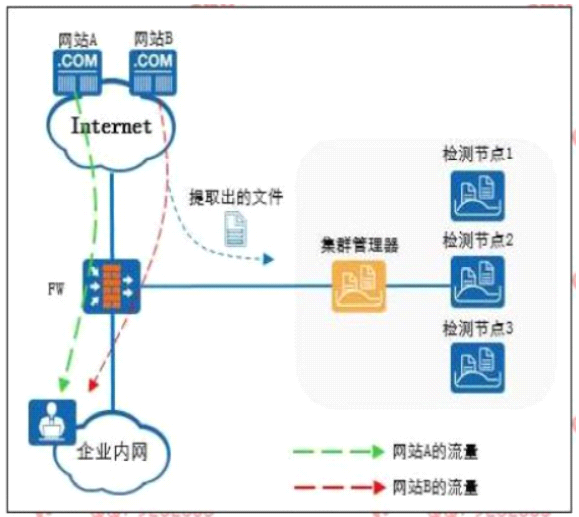
The Web reputation function is enabled on the firewall, and website A is set as a trusted website and website B is set as a suspicious website.
Which of the following statements is correct
Which of the following options does not belong to the security risk of the application layer of the TCP/IP protocol stack?
Regarding scanning and snooping attacks, which of the following descriptions is wrong?