At ValidExamDumps, we consistently monitor updates to the HPE6-A84 exam questions by HP. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the HP Aruba Certified Network Security Expert Written Exam exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by HP in their HPE6-A84 exam. These outdated questions lead to customers failing their HP Aruba Certified Network Security Expert Written Exam exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the HPE6-A84 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.
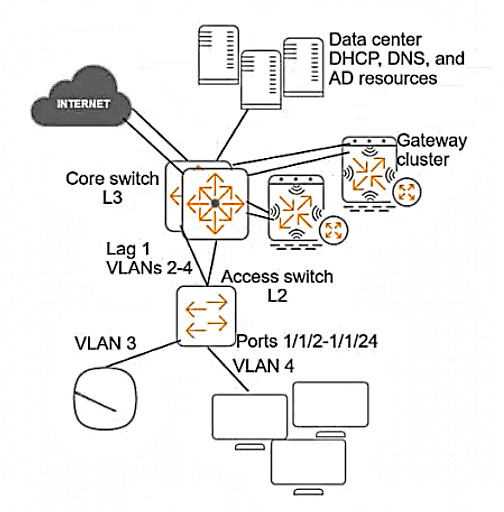
A customer requires protection against ARP poisoning in VLAN 4. Below are listed all settings for VLAN 4 and the VLAN 4 associated physical interfaces on the AOS-CX access layer switch:
What is one issue with this configuration?
B) LAG 1 is configured as trusted for ARP inspection but should be untrusted. This is not an issue because LAG 1 connects to the core switch, which is a trusted device that does not send forged ARP packets.
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the ''eth-internet" role. The gateway should also handle assigning clients to their VLAN, which is VLAN 20.
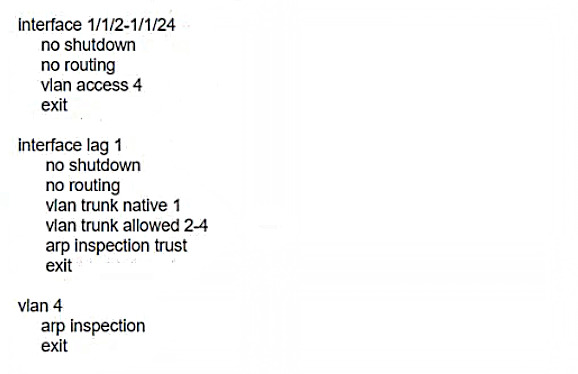
The plan for the enforcement policy and profiles is shown below:
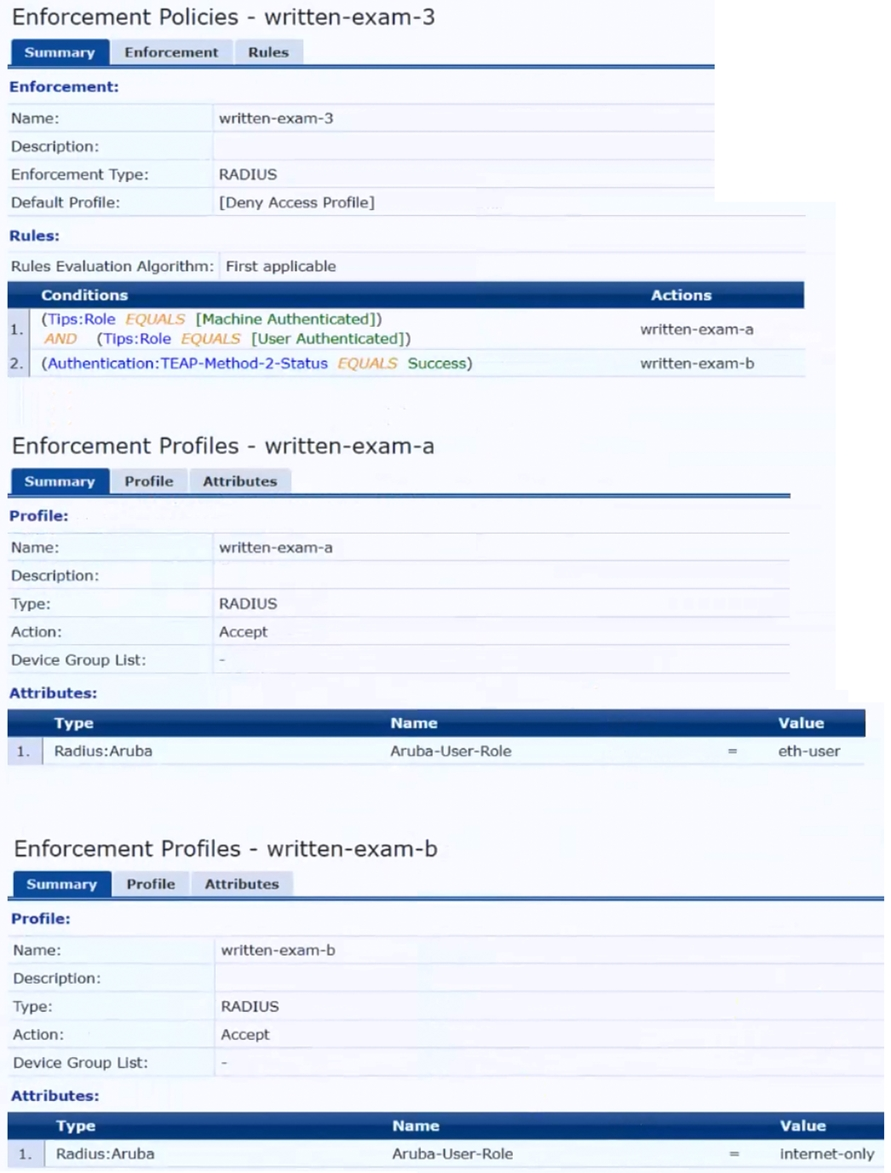
The gateway cluster has two gateways with these IP addresses:
* Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
* Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
* VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
What is one change that you should make to the solution?
A customer has an AOS 10-based mobility solution, which authenticates clients to Aruba ClearPass Policy Manager (CPPM). The customer has some wireless devices that support WPA2 in personal mode only.
How can you meet these devices' needs but improve security?
MPSK (Multi Pre-Shared Key) is a feature that allows assigning different pre-shared keys (PSKs) to different devices or groups of devices on the same WLAN. MPSK improves security over WPA2 in personal mode, which uses a single PSK for all devices on the WLAN. With MPSK, you can create and manage multiple PSKs, each with its own role, policy, and expiration date. You can also revoke or change a PSK for a specific device or group without affecting other devices on the WLAN. MPSK is compatible with devices that support WPA2 in personal mode only, as they do not need to support any additional protocols or certificates.
To use MPSK on the WLAN to which the devices connect, you need to enable MPSK in the WLAN settings and configure the PSKs in Aruba ClearPass Policy Manager (CPPM). You can find more information about how to configure MPSK in the [Configuring Multi Pre-Shared Key - Aruba] page and the [ClearPass Policy Manager User Guide] . The other options are not correct because they either do not improve security or are not applicable for devices that support WPA2 in personal mode only. For example, configuring WIDS policies that apply extra monitoring to these particular devices would not prevent them from being compromised or spoofed, but rather detect and mitigate potential attacks. Connecting these devices to the same WLAN to which 802.1X-capable clients connect, using MAC-Auth fallback, would not provide strong authentication or encryption, as MAC addresses can be easily spoofed or captured. Enabling dynamic authorization (RFC 3576) in the AAA profile for the devices would not affect the authentication process, but rather allow CPPM to change the attributes or status of a user session on the controller without requiring re-authentication.
Refer to the scenario.
A hospital has an AOS10 architecture that is managed by Aruba Central. The customer has deployed a pair of Aruba 9000 Series gateways with Security licenses at each clinic. The gateways implement IDS/IPS in IDS mode.
The Security Dashboard shows these several recent events with the same signature, as shown below:
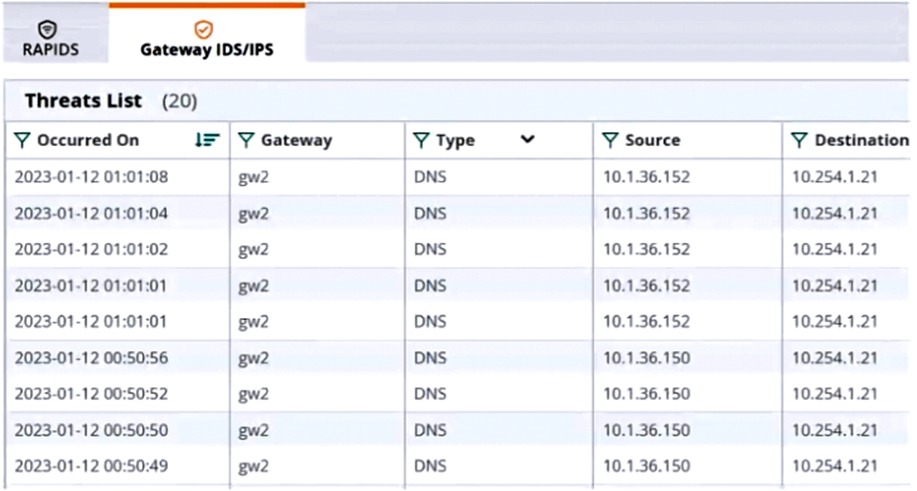
Which step could give you valuable context about the incident?
Refer to the scenario.
A customer is migrating from on-prem AD to Azure AD as its sole domain solution. The customer also manages both wired and wireless devices with Microsoft Endpoint Manager (Intune).
The customer wants to improve security for the network edge. You are helping the customer design a ClearPass deployment for this purpose. Aruba network devices will authenticate wireless and wired clients to an Aruba ClearPass Policy Manager (CPPM) cluster (which uses version 6.10).
The customer has several requirements for authentication. The clients should only pass EAP-TLS authentication if a query to Azure AD shows that they have accounts in Azure AD. To further refine the clients' privileges, ClearPass also should use information collected by Intune to make access control decisions.
The customer wants you to configure CPPM to collect information from Intune on demand during the authentication process.
What should you tell the Intune admins about the certificates issued to clients?
The certificates issued to clients do not need to be issued by a well-known, trusted CA, as long as ClearPass trusts the CA that issued them. The certificates do not need to include the client MAC address in the subject name, as this is not relevant for querying Intune. The certificates do not need to be issued by a ClearPass Onboard CA, as this is not a requirement for using the Intune extension.