At ValidExamDumps, we consistently monitor updates to the HashiCorp HCVA0-003 exam questions by HashiCorp. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the HashiCorp Certified: Vault Associate (003) Exam exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by HashiCorp in their HashiCorp HCVA0-003 exam. These outdated questions lead to customers failing their HashiCorp Certified: Vault Associate (003) Exam exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the HashiCorp HCVA0-003 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Your organization uses a CI/CD pipeline to deploy its applications on Azure. During testing, you generate new credentials to validate Vault can create new credentials. The result of this command is below:
text
CollapseWrapCopy
$ vault read azure/creds/bryan-krausen
Key Value
--- -----
lease_id azure/creds/bryan-krausen/9eed0373-ca92-99b6-b914-779b7bb0e1d9
lease_duration 60m
lease_renewable true
client_id 532bf678-ee4e-6be1-116b-4e4221e445dd
client_secret be60395b-4e6b-2b7e-a4b3-c449a5c00973
What commands can be used to revoke this secret after you have finished testing? (Select three)
Comprehensive and Detailed In-Depth
Dynamic credentials are tracked by leases, revocable via vault lease revoke. The Vault documentation states:
'The vault lease revoke command is used to revoke a lease/secret created by a Vault secrets engine. Each lease that is created is tracked using a unique lease ID, which can be used to renew or revoke a lease.
You can revoke an individual lease using the command vault lease revoke <lease_id>
You can also revoke ALL leases from a secrets engine using the -prefix flag, such as vault lease revoke -prefix azure/
You can also revoke leases created from a specific role by using the -prefix flag but specifying the path all the way to the role like this: vault lease revoke -prefix azure/creds/<role_name>'
--- Vault Commands: lease revoke
B: Correct. vault lease revoke -prefix azure/ revokes all leases under azure/.
C: Correct. vault lease revoke azure/creds/bryan-krausen/9eed0373-ca92-99b6-b914-779b7bb0e1d9 targets the specific lease ID.
E: Correct. vault lease revoke -prefix azure/creds/bryan-krausen revokes all leases for that role.
A: Incorrect; lacks the -prefix flag, making it invalid syntax.
D: Incorrect; lacks the -prefix flag and isn't a full lease ID.
Vault Commands: lease revoke
From the options below, select the benefits of using a batch token over a service token (select four).
Comprehensive and Detailed in Depth
Batch tokens are lightweight alternatives to service tokens, with trade-offs. Let's analyze:
A: Designed for short-lived, high-performance tasks. Correct.
B: Cannot be root tokens; root status is service-token-specific. Incorrect.
C: Orphan batch tokens work in replication. Correct.
D: No accessors; unique to service tokens. Incorrect.
E: Minimal overhead makes them scalable. Correct.
F: No disk storage reduces cost. Correct.
Overall Explanation from Vault Docs:
''Batch tokens are encrypted blobs... lightweight, scalable, no storage cost, ideal for ephemeral workloads.''
After creating a dynamic credential on a database, the DBA accidentally deletes the credentials on the database itself. When attempting to remove the lease, Vault returns an error stating that the credential cannot be found. What command can be run to make Vault remove the secret?
Comprehensive and Detailed in Depth
When a dynamic credential is deleted externally, Vault may fail to revoke the lease due to the missing backend secret. The HashiCorp Vault documentation states: 'The -force flag is meant for recovery situations where the secret in the target platform was manually removed.' The command vault lease revoke -force -prefix <lease_path> allows Vault to forcibly revoke all leases under the specified prefix, bypassing the error.
The docs elaborate: 'Using -force with -prefix will revoke all leases that match the given prefix, even if the underlying secrets cannot be found or revoked on the target system. This is useful for cleaning up Vault's lease table when external changes disrupt normal revocation.' Here, <lease_path> would be the path like database/creds/role/. B (vault lease -renew) renews leases, not removes them. C (-enforce) is not a valid flag. D (vault revoke -apply) is incorrect syntax. Thus, A is correct.
HashiCorp Vault Documentation - Lease Revoke Command: Force
A user is assigned the following policy, and they can successfully retrieve secrets using the CLI. However, the user reports receiving an error message in the UI. Why can't the user access the secret in the Vault UI?
path "kv/apps/app01" { capabilities = ["read"] }
Successful retrieval using the CLI
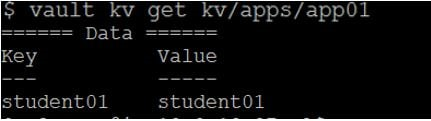
(Error: Permission denied in UI)
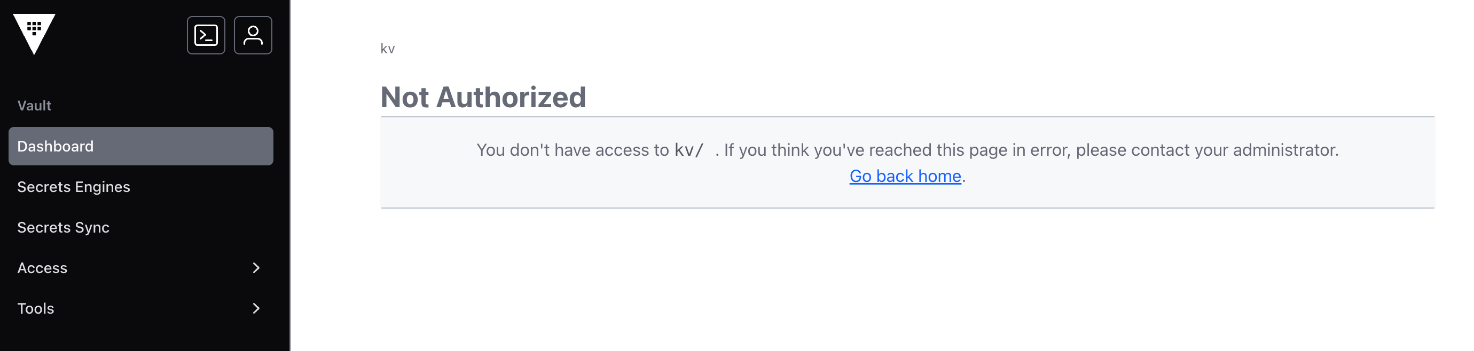
Comprehensive and Detailed in Depth
A: Irrelevant to permissions. Incorrect.
B: UI and CLI use the same permissions. Incorrect.
C: UI browsing requires list on parent paths; read alone isn't enough. Correct.
D: Token works via CLI, so it's valid. Incorrect.
Overall Explanation from Vault Docs: ''To browse the UI, users need list permissions on paths leading to the secret...'' Reference: https://developer.hashicorp.com/vault/docs/concepts/policies#list
''To browse the UI, users need list permissions on paths leading to the secret...''
Overall Explanation from Vault Docs: ''To browse the UI, users need list permissions on paths leading to the secret...'' Reference: https://developer.hashicorp.com/vault/docs/concepts/policies#list
You have been tasked with writing a policy that will allow read permissions for all secrets at path secret/bar. The users that are assigned this policy should also be able to list the secrets. What should this policy look like?
A.

B.
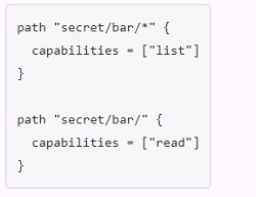
C.
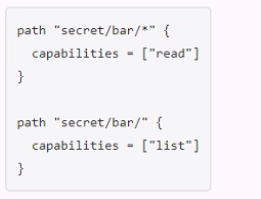
D.
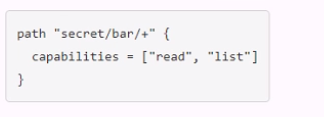
The other options are not correct because they either grant too much or too little permissions. Option A would grant both read and list permissions to all secrets under secret/bar, which is more than what is required. Option B would grant list permissions to all secrets under secret/bar, but only read permissions to secret/bar itself, which is not what is required. Option D would use an invalid character (+) in the policy, which would cause an error.
Policy Syntax | Vault | HashiCorp Developer