At ValidExamDumps, we consistently monitor updates to the GIAC GCCC exam questions by GIAC. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the GIAC Critical Controls Certification exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by GIAC in their GIAC GCCC exam. These outdated questions lead to customers failing their GIAC Critical Controls Certification exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the GIAC GCCC exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
An attacker is able to successfully access a web application as root using ' or 1 = 1 . as the password. The successful access
indicates a failure of what process?
A security incident investigation identified the following modified version of a legitimate system file on a compromised client:
C:\Windows\System32\winxml.dll Addition Jan. 16, 2014 4:53:11 PM
The infection vector was determined to be a vulnerable browser plug-in installed by the user. Which of the organization's CIS Controls failed?
Allied services have recently purchased NAC devices to detect and prevent non-company owned devices from attaching to their internal wired and wireless network. Corporate devices will be automatically added to the approved device list by querying Active Directory for domain devices. Non-approved devices will be placed on a protected VLAN with no network access. The NAC also offers a web portal that can be integrated with Active Directory to allow for employee device registration which will not be utilized in this deployment. Which of the following recommendations would make NAC installation more secure?
A global corporation has major data centers in Seattle, New York, London and Tokyo. Which of the following is the correct approach from an intrusion detection and event correlation perspective?
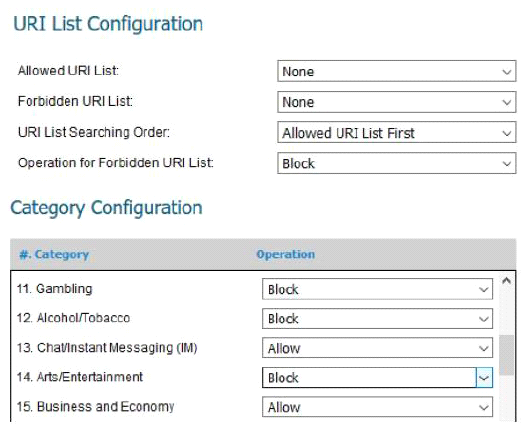
Below is a screenshot from a deployed next-generation firewall. These configuration settings would be a defensive measure for which CIS Control?