At ValidExamDumps, we consistently monitor updates to the Fortinet NSE7_PBC-7.2 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet NSE 7 - Public Cloud Security 7.2 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet NSE7_PBC-7.2 exam. These outdated questions lead to customers failing their Fortinet NSE 7 - Public Cloud Security 7.2 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet NSE7_PBC-7.2 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You need a solution to safeguard public cloud-hosted web applications from the OWASP Top 10 vulnerabilities. The solution must support the same region in which your applications reside, with minimum traffic cost
Which solution meets the requirements?
The correct answer is C. Use FortiWebCloud.
The other options are incorrect because:
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs.
What are the two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose two.)
The two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub are
A . ExpressRoute and E. VPN Gateway.
The other options are incorrect because:
An L2TP connection is not a supported connectivity option for Azure vWAN. L2TP is a protocol that creates a tunnel between two endpoints at the data link layer (Layer 2) of the OSI model. L2TP is not compatible with the Azure vWAN hub.
You are troubleshooting an Azure SDN connectivity issue with your FortiGate VM
Which two queries does that SDN connector use to interact with the Azure management API? (Choose two.)
Refer to Exhibit:
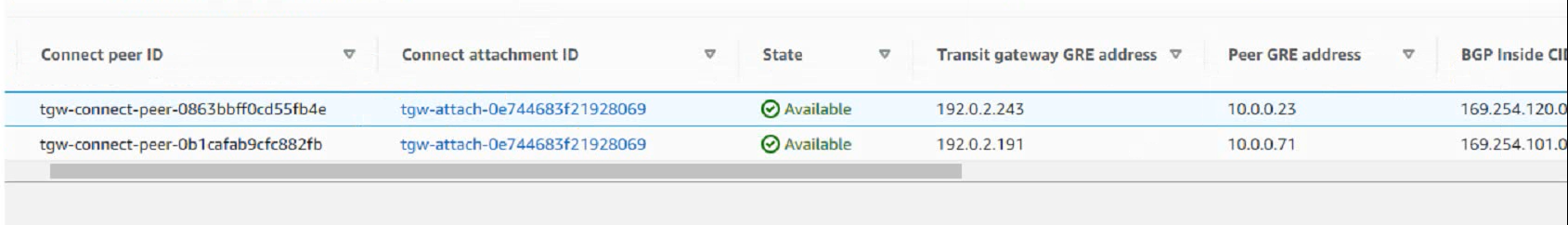
The exhibit shows the Connect Peers settings on Amazon Web Services (AWS) transit gateway attachments With two FortiGate VMS in a security VPC.
Which two statements are correct? (Choose two.)
The other options are incorrect because:
Refer to the exhibit

You deployed an HA active-passive FortiGate VM in Microsoft Azure.
Which two statements regarding this particular deployment are true? (Choose two.)