At ValidExamDumps, we consistently monitor updates to the Fortinet NSE6_FSW-7.2 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet NSE 6 - FortiSwitch 7.2 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet NSE6_FSW-7.2 exam. These outdated questions lead to customers failing their Fortinet NSE 6 - FortiSwitch 7.2 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet NSE6_FSW-7.2 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Which feature should you enable to reduce the number or unwanted IGMP reports processed by the IGMP querier?
Enable IGMP snooping proxy (C): To reduce the number of unwanted IGMP reports processed by the IGMP querier, enabling IGMP snooping proxy is effective. This feature acts as an intermediary between multicast routers and hosts, optimizing the management of IGMP messages by handling report messages locally and reducing unnecessary IGMP traffic across the network. This minimizes the processing load on the IGMP querier and improves overall network efficiency.
Refer to the exhibit.
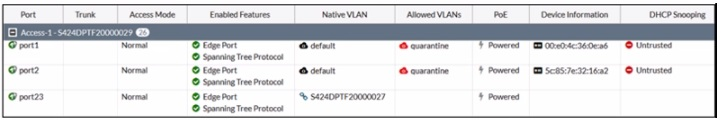
The exhibit shows the current status of the ports on the managed FortiSwitch. Access-1.
Why would FortiGate display a serial number in the Native VLAN column associated with the port23 entry?
The information in the 'Native VLAN' column for port23 on the FortiSwitch indicates that a standalone switch is connected to it. This is because the column displays '$424MPTF20000027,' which matches the format of a Fortinet device serial number.
Here's a breakdown of the evidence in the image:
Native VLAN: The 'Native VLAN' column typically displays the VLAN ID for untagged traffic on a trunk port. However, in this case, it shows a serial number format ('$424MPTF20000027').
No Trunk Information: The 'Trunk' column is blank for port23, indicating it's not configured as a trunk member.
Other Ports: Port1 and port2 show 'default' in the 'Native VLAN' column, which is the expected behavior for access ports.
Fortinet FortiSwitch devices typically don't display the serial number of adjacent FortiSwitch devices in the 'Native VLAN' column. This column is reserved for VLAN information on trunk ports.
Exhibit.
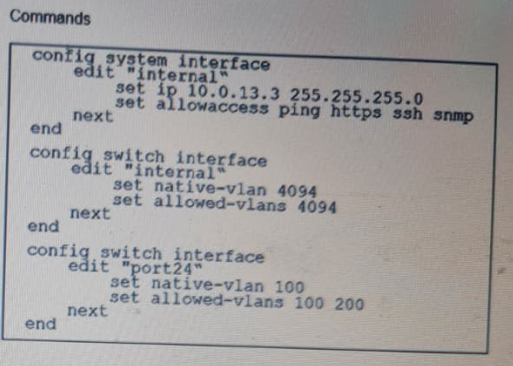
port24 is the only uplink port connected to the network where access to FortiSwitch management services is possible. However, FortiSwitch is still not accessible on the management interface. Which two actions should you take to fix the issue and access FortiSwitch? (Choose two.)
To enable access to the FortiSwitch management interface from the network, certain configuration adjustments need to be made, particularly considering the VLAN settings displayed in the exhibit:
Adding port24 native VLAN to the allowed VLANs on internal (Option A): The management VLAN (VLAN 4094 in this case, as it is set as the native VLAN on the 'internal' interface of the FortiSwitch) must be included in the allowed VLANs on the interface that provides management connectivity. Since port24 is set with a different native VLAN (VLAN 100), VLAN 4094 (the management VLAN) should be allowed through to ensure connectivity.
Allow VLAN ID 4094 on port24 if management traffic is tagged (Option C): Management traffic is tagged on VLAN 4094. Since port24 is connected to the network and serves as an uplink, allowing VLAN 4094 ensures that management traffic can reach the management interface of the FortiSwitch through this port.
The changes align with Fortinet's best practices for setting up management VLANs and ensuring they are permitted on the relevant switch ports for proper management traffic flow.
FortiGate Infrastructure and Security 7.2 Study Guides
Best practices for VLAN configurations in Fortinet's technical documentation
How does FortiSwitch perform actions on ingress and egress traffic using the access control list (ACL)?
In FortiSwitch, Access Control Lists (ACLs) are used to enforce security rules on both ingress and egress traffic:
ACL Evaluation Order (D):
Operational Function: FortiSwitch processes ACL entries from top to bottom, similar to how firewall rules are processed. The first match in the ACL determines the action taken on the packet, whether to allow or deny it, making the order of rules critical.
Configuration Advice: Careful planning of the order of ACL rules is necessary to ensure that more specific rules precede more general ones to avoid unintentional access or blocks.
Refer to the diagnostic output:

Two entries in the exhibit show that the same MAC address has been used in two different VLANs. Which MAC address is shown in the above output?
The MAC address '00:50:56:96:e3:fc' appearing in two different VLANs (4089 and 4094) in the diagnostic output indicates it is a MAC address associated with a device that supports traffic from multiple VLANs. Such a behavior is typical of network infrastructure devices like switches or routers, which are configured to allow traffic from various VLANs to pass through a single physical or logical interface. This is essential in network designs that utilize VLANs to segregate network traffic for different departments or use cases while using the same physical infrastructure.