At ValidExamDumps, we consistently monitor updates to the Fortinet NSE6_FML-6.4 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet NSE 6 - FortiMail 6.4 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet NSE6_FML-6.4 exam. These outdated questions lead to customers failing their Fortinet NSE 6 - FortiMail 6.4 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet NSE6_FML-6.4 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.
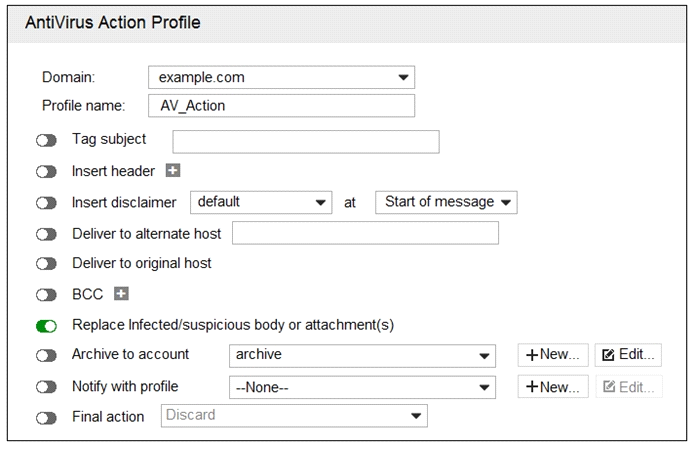
What are two expected outcomes if FortiMail applies this antivirus action profile to an email? (Choose two.)
FortiMail is configured with the protected domain example.com.
Which two envelope addresses will require an access receive rule, to relay for unauthenticated senders? (Choose two.)
Refer to the exhibit.
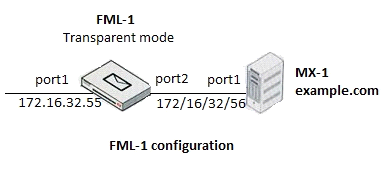
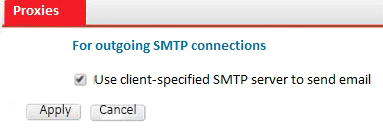
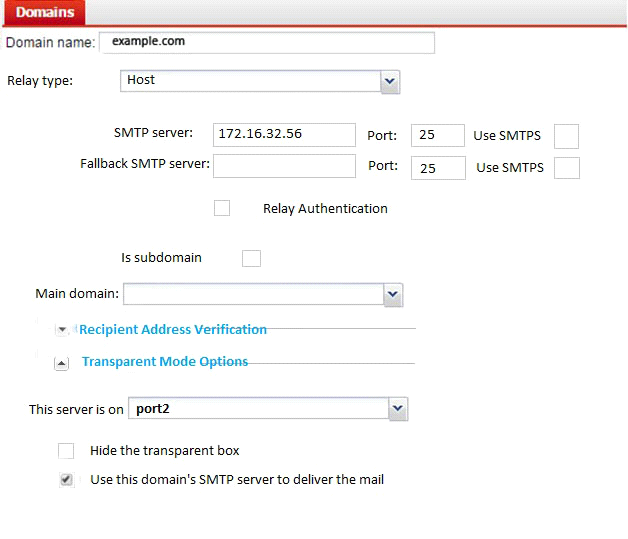
Which of the following statements are true regarding the transparent mode FortiMail's email routing for the example.com domain? (Choose two.)
Which FortiMail option removes embedded code components in Microsoft Word, while maintaining the original file format?
Examine the FortiMail IBE service configuration shown in the exhibit; then answer the question below.
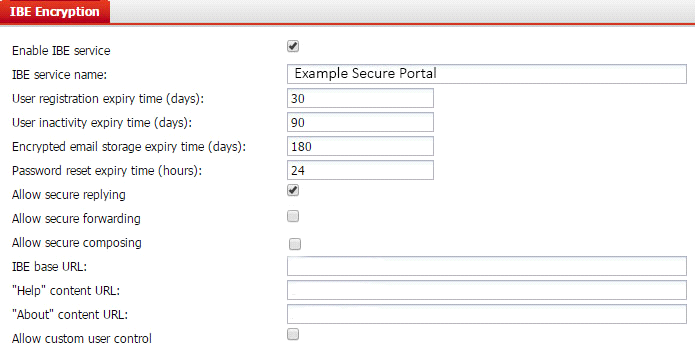
Which of the following statements describes the User inactivity expiry time of 90 days?