At ValidExamDumps, we consistently monitor updates to the Fortinet NSE5_FNC_AD_7.6 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet NSE 5 - FortiNAC-F 7.6 Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet NSE5_FNC_AD_7.6 exam. These outdated questions lead to customers failing their Fortinet NSE 5 - FortiNAC-F 7.6 Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet NSE5_FNC_AD_7.6 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
An administrator manages a corporate environment where all users log into the corporate domain each time they connect to the network. The administrator wants to leverage login scripts to use a FortiNAC-F agent to enhance endpoint visibility
Which agent can be deployed as part of a login script?
In a corporate domain environment where 'enhanced endpoint visibility' is required, the Persistent Agent is the recommended choice. Unlike the Dissolvable Agent, which is temporary and intended for one-time compliance scans during registration, the Persistent Agent is an 'install-and-stay-resident' application.
The Persistent Agent is specifically designed to be distributed through automated enterprise methods, including login scripts, Group Policy Objects (GPO), or third-party software management tools. When deployed via a login script, the agent can be configured to silently install and immediately begin communicating with the FortiNAC-F service interface. Once active, it provides continuous visibility by reporting host details such as logged-on users, installed applications, and adapter information. It also listens for Windows session events (logon/logoff) to trigger automatic single-sign-on (SSO) registration in FortiNAC-F, ensuring that as soon as a user connects to the domain, their device is identified and assigned the correct network access policy.
'The Persistent Agent can be distributed to Windows domain machines via login script or by any other software distribution method your organization might use. The Persistent Agent remains installed on the host at all times. Once the agent is installed it runs in the background and communicates with FortiNAC at intervals established by the FortiNAC administrator.' --- FortiNAC-F Administration Guide: Persistent Agent Overview.
Refer to the exhibit.
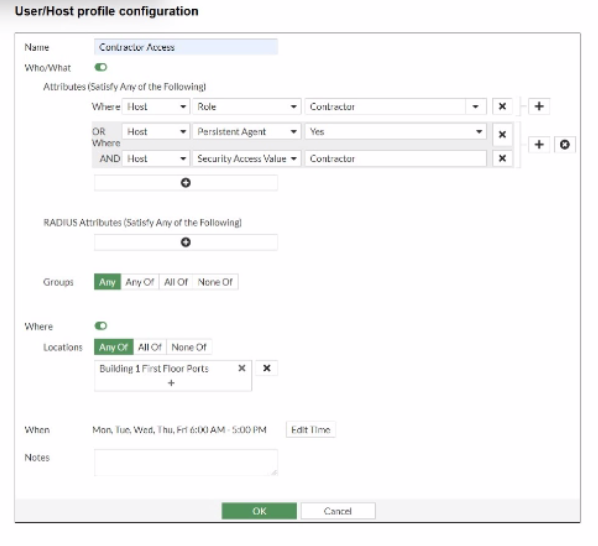
If a host is connected to a port in the Building 1 First Floor Ports group, what must also be true to match this user/host profile?
The User/Host Profile in FortiNAC-F is the fundamental logic engine used to categorize endpoints for policy assignment. As seen in the exhibit, the configuration uses a combination of Boolean logic operators (OR and AND) to define the 'Who/What' attributes.
According to the FortiNAC-F Administrator Guide, attributes grouped together within the same bracket or connected by an OR operator require only one of those conditions to be met. In the exhibit, the first two attributes are 'Host Role = Contractor' OR 'Host Persistent Agent = Yes'. This forms a single logical block. This block is then joined to the third attribute ('Host Security Access Value = Contractor') by an AND operator. Consequently, a host must satisfy at least one of the first two conditions AND satisfy the third condition to match the 'Who/What' section.
Furthermore, the profile includes Location and When (time) constraints. The exhibit shows the location is restricted to the 'Building 1 First Floor Ports' group. The 'When' schedule is explicitly set to Mon-Fri 6:00 AM - 5:00 PM. For a profile to match, all enabled sections (Who/What, Locations, and When) must be satisfied simultaneously. Therefore, the host must meet the conditional contractor/agent criteria, possess the specific security access value, and connect during the defined 6 AM to 5 PM window.
'User/Host Profiles use a combination of attributes to identify a match. Attributes joined by OR require any one to be true, while attributes joined by AND must all be true. If a Schedule (When) is applied, the host must also connect within the specified timeframe for the profile to be considered a match. All criteria in the Who/What, Where, and When sections are cumulative.' --- FortiNAC-F Administration Guide: User/Host Profile Configuration.
A network administrator is troubleshooting a network access issue for a specific host. The administrator suspects the host is being assigned a different network access policy than expected.
Where would the administrator look to identify which network access policy, if any, is being applied to a particular host?
When troubleshooting network access in FortiNAC-F, it is often necessary to verify exactly why a host has been granted a specific level of access. Since FortiNAC-F evaluates policies from the top down and assigns access based on the first match, an administrator needs a clear way to see the results of this evaluation for a specific live endpoint.
The Policy Details (C) view is the designated tool for this purpose. By navigating to the Hosts > Hosts (or Adapter View) in the Administration UI, an administrator can search for the specific MAC address or IP of the host in question. Right-clicking on the host record reveals a context menu from which Policy Details can be selected. This view provides a real-time 'look' into the policy engine's decision for that specific host, showing the Network Access Policy that was matched, the User/Host Profile that triggered the match, and the resulting Network Access Configuration (VLAN/ACL) currently applied.
While Policy Logs (A) provide a historical record of all policy transitions across the system, they are often too high-volume to efficiently find a single host's current state. The Connections view (B) shows the physical port and basic status but lacks the granular policy logic breakdown. The Port Properties (D) view shows the configuration of the switch interface itself, which is only one component of the final access determination.
'To identify which policy is currently applied to a specific endpoint, use the Policy Details view. Navigate to Hosts > Hosts, select the host, right-click and choose Policy Details. This window displays the specific Network Access Policy, User/Host Profile, and Network Access Configuration currently in effect for that host record.' --- FortiNAC-F Administration Guide: Policy Details and Troubleshooting.
Which two requirements must be met to set up an N+1 HA cluster? (Choose two.)
The N+1 High Availability (HA) architecture was introduced in FortiNAC-F version 7.6 to provide a more scalable and flexible redundancy model compared to the traditional 1+1 active/passive setup. In an N+1 configuration, a single secondary (standby) appliance can provide coverage for multiple primary (active) Control and Application (CA) appliances.
To set up an N+1 HA cluster, there are two fundamental structural requirements:
A FortiNAC-F Manager (FortiNAC-M): Unlike standard 1+1 HA, which can be configured directly between two CAs, N+1 management is centralized. The FortiNAC-M acts as the orchestrator that manages the failover groups, monitors the health of the primaries, and coordinates the promotion of the secondary server if a primary fails.
A FortiNAC-F device designated as a Secondary: The cluster must have one appliance explicitly configured with the Secondary failover role. This device remains in a standby state, receiving database replications from all N primaries in its group until it is called upon to take over the functions of a failed unit.
While a cluster can support multiple primaries (D), it does not strictly require 'at least two' to function as an N+1 group; it simply requires N primaries (where N 1). Additionally, N+1 is typically a Layer 3 managed solution via the Manager, meaning it does not mandate a 'dedicated VLAN' for synchronization like some Layer 2 HA deployments.
'In FortiNAC-F 7.6, FortiNAC-M functions as a manager to manage the N+1 Failover Groups... enabling N+M high availability for CAs. To create an N+1 Failover group, you should add the secondary CA to the FortiNAC-M first, then add the primary CAs. The secondary CA is designed to take over the functionality of any single failed primary component.' --- FortiNAC-F 7.6.0 N+1 Failover Reference Manual.
When creating a device profiling rule, what are two advantages of registering the device in the host view? (Choose two.)
In FortiNAC-F, the Device Profiler is a rule-based engine that evaluates unknown 'rogue' devices and classifies them based on fingerprints and behavior. When a profiling rule matches a device, the administrator can configure the rule to automatically register that device. The registration process can place the device record in two primary locations: the Topology View (as a device) or the Host View (as a registered host).
According to the FortiNAC-F Administration Guide, registering a device in the Host View provides significant advantages for identity management and historical tracking. First, the devices can be associated with a user (C). In the FortiNAC database architecture, the Host View is the primary repository for endpoint identity; placing a profiled device here allows the system to link that hardware (MAC address) to a specific user account, whether that user is an employee, guest, or a system-level 'owner'. This association is essential for Role-Based Access Control (RBAC) and for tracking accountability across the network fabric.
Second, devices registered in the Host View will have connection logs (B). FortiNAC-F maintains a detailed operational history for all host records, including every instance of the device connecting to or disconnecting from a port, its IP address assignments, and the specific policies applied during each session. These logs are invaluable for troubleshooting connectivity issues and for security forensic audits, as they provide a clear timeline of the device's lifecycle on the network. In contrast, devices managed only in the Topology View are typically treated as infrastructure components where the focus is on device availability rather than individual session history.
'Devices that are registered and associated with a user are placed in the Host View and removed from the Profiled Devices window... Placing a device in the Host View allows for the tracking of connection history and the association of the device with a specific identity or user record within the FortiNAC database.' --- FortiNAC-F Administration Guide: Device Profiler How it Works.