At ValidExamDumps, we consistently monitor updates to the Fortinet NSE4_FGT_AD-7.6 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet NSE 4 - FortiOS 7.6 Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet NSE4_FGT_AD-7.6 exam. These outdated questions lead to customers failing their Fortinet NSE 4 - FortiOS 7.6 Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet NSE4_FGT_AD-7.6 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibits.

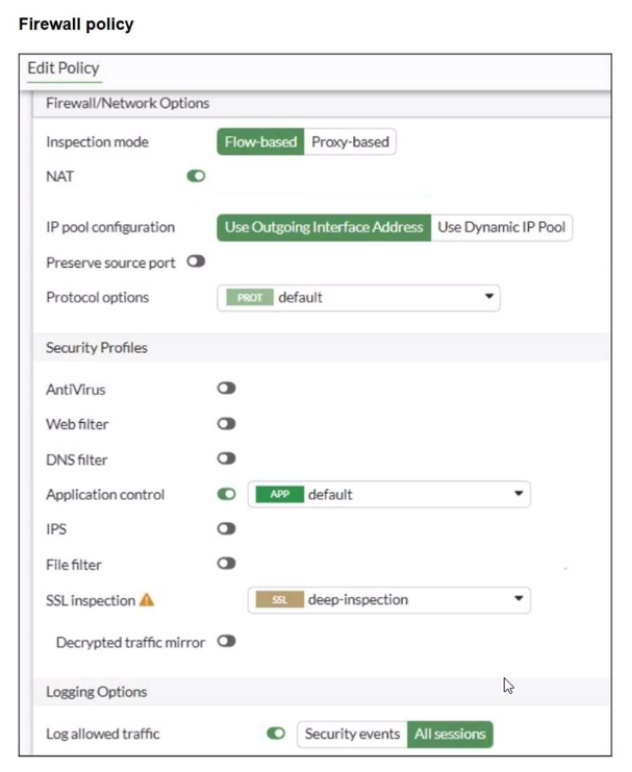
You have implemented the application sensor and the corresponding firewall policy as shown in the exhibits.
Which two factors can you observe from these configurations? (Choose two.)
From the exhibits:
The Application Control sensor has these key settings:
Application and Filter Overrides
Priority 1: Excessive-Bandwidth (Type: Filter) with Action Block
Priority 2: Google (Type: Filter) with Action Monitor
Category actions shown include Social Media set to Block (this category includes Facebook).
The firewall policy is using:
Flow-based inspection
Application control enabled (profile: default)
Deep inspection enabled (helps identify applications inside HTTPS)
Logging enabled
FortiOS applies Application Control as follows (top-down within the Application Control profile):
Overrides are evaluated by priority (highest priority first).
The first matching override determines the action (block/monitor/allow) for that traffic.
Category-based actions apply to applications that fall into those categories unless an override matches first.
Why A is correct
A . YouTube access is blocked based on Excessive-Bandwidth Application and Filter override settings.
The profile explicitly blocks the Excessive-Bandwidth behavior filter at the highest override priority.
When YouTube traffic is detected as matching the Excessive-Bandwidth behavior, FortiGate will apply the Block action due to the override.
Because this is a priority override, it is enforced before lower-priority entries.
Why B is correct
B . Facebook access is blocked based on the category filter settings.
The Application Sensor shows Social Media configured with a Block action.
Facebook is categorized under Social Media, so it will be blocked when matched by Application Control.
Why C is not correct
C . Facebook access is allowed but you cannot play Facebook videos...
Since the Social Media category is set to Block, Facebook would be blocked at the category level (not merely video playback).
Why D is not correct
D . YouTube search is allowed based on the Google override...
The Google override action is Monitor, not Allow.
''Monitor'' logs/detects but does not override a block condition to ''allow'' traffic.
Also, YouTube traffic is not guaranteed to be treated as ''Google'' in a way that would permit it, and any matching block condition (such as Excessive-Bandwidth) would still take precedence.
Refer to the exhibits.
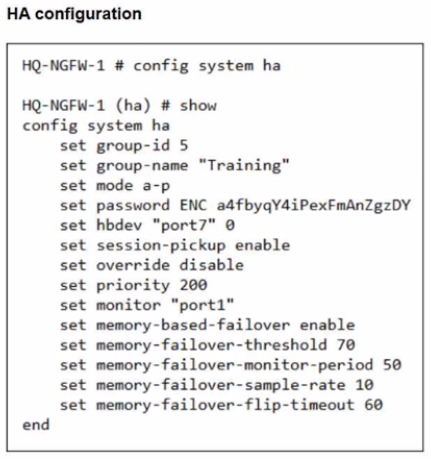
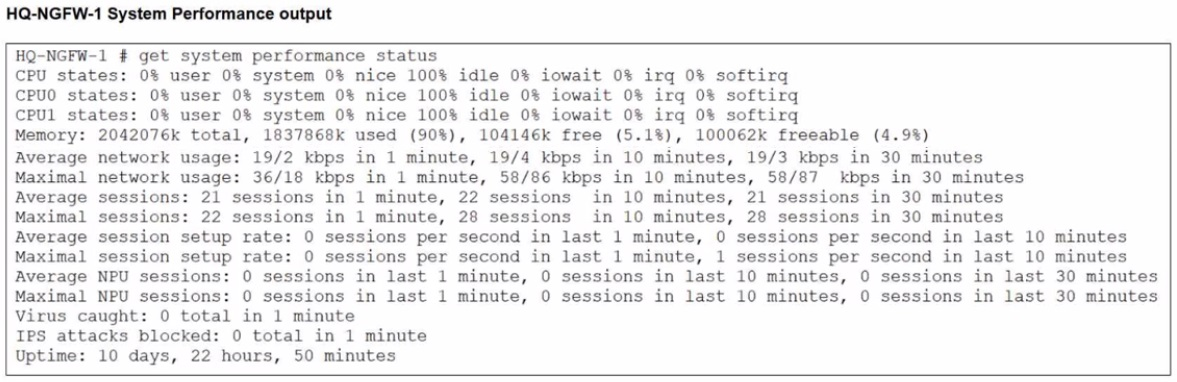
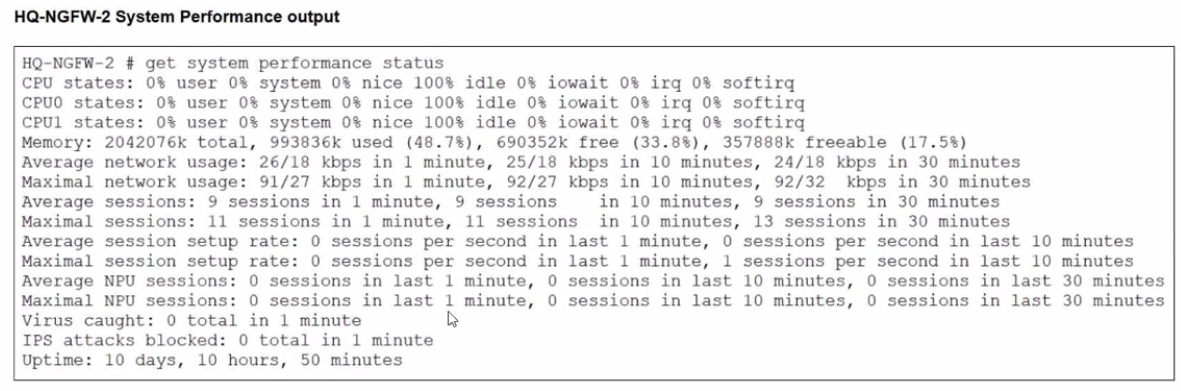
An administrator has observed the performance status outputs on an HA cluster for 55 seconds.
Which FortiGate is the primary?
From the HA configuration shown for HQ-NGFW-1:
set memory-based-failover enable
set memory-failover-threshold 70
set memory-failover-monitor-period 50
set memory-failover-sample-rate 10
set memory-failover-flip-timeout 60
set override disable
set priority 200
From the performance status outputs:
HQ-NGFW-1 memory used is 90% (well above the configured threshold of 70%)
HQ-NGFW-2 memory used is about 48.7% (well below the threshold)
What happens in FortiOS 7.6 with memory-based failover
When memory-based failover is enabled, FortiGate monitors memory utilization. If the unit's memory usage stays above the configured memory-failover-threshold for the configured memory-failover-monitor-period, the cluster triggers a failover away from the unit under memory pressure.
Threshold = 70%
HQ-NGFW-1 is at 90%, so it violates the threshold.
Monitor period = 50 seconds.
The administrator observed for 55 seconds, which is longer than 50 seconds, so the condition is met for long enough to trigger failover.
The memory-failover-flip-timeout 60 is used to prevent rapid back-and-forth role changes (flapping) after a failover decision; it does not prevent the initial failover from occurring once the threshold breach persists for the monitor period.
Which three statements about SD-WAN performance SLAs are true? (Choose three.)
In FortiOS 7.6, SD-WAN Performance SLAs are used to measure link quality and influence SD-WAN rule decisions. The following three statements are true.
C . All the SLA targets can be configured.
True
SD-WAN Performance SLAs allow administrators to configure:
Latency
Jitter
Packet loss
Mean Opinion Score (MOS) (for voice)
Threshold values for these metrics are fully configurable per SLA.
This is explicitly documented in the SD-WAN Performance SLA configuration section.
D . They are applied in an SD-WAN rule lowest cost strategy.
True
Performance SLAs are commonly used with the Lowest Cost (SLA-based) strategy.
In this strategy:
FortiGate selects the lowest-cost link that meets the SLA requirements.
If a link violates the SLA, it is excluded from selection.
E . They can be measured actively or passively.
True
FortiOS supports:
Active probing (synthetic probes such as ping/HTTP)
Passive measurement (based on real traffic statistics)
Administrators can choose how SLAs are measured depending on the deployment and requirements.
Why the other options are incorrect
A . They rely on session loss and jitter.
Incorrect
SLAs measure packet loss, latency, and jitter.
Session loss is not an SLA metric in FortiOS.
B . They monitor the state of the FortiGate device.
Incorrect
Performance SLAs monitor link quality, not FortiGate system health or device state.
Refer to the exhibit
A firewall policy to enable active authentication is shown.

When attempting to access an external website using an active authentication method, the user is not presented with a login prompt. What is the most likely reason for this situation?
Based on the exhibit and FortiOS 7.6 Active Authentication (captive portal) behavior, the most likely reason the user is not presented with a login prompt is that DNS is missing from the firewall policy.
What the exhibit shows
The firewall policy configured for active authentication includes:
Source: HQ_SUBNET and Remote-users
Destination: all
Services:
HTTP
HTTPS
ALL_ICMP
Security Profiles: Web filter and SSL inspection enabled
Authentication: Active (user group referenced)
DNS is not included as a service in the policy.
Why DNS is required for active authentication
In FortiOS 7.6, active authentication (captive portal) works as follows:
The user attempts to access a website using a URL (for example, www.example.com).
The client must first perform a DNS lookup to resolve the domain name.
FortiGate intercepts the initial HTTP/HTTPS request and redirects the user to the authentication portal.
If DNS traffic is blocked or not allowed:
The hostname cannot be resolved.
The HTTP/HTTPS request never properly occurs.
FortiGate has nothing to intercept, so the login prompt is never triggered.
This is explicitly documented in the FortiOS 7.6 Authentication and Captive Portal requirements, which state that DNS must be permitted for captive portal--based authentication to function correctly.
Why the other options are incorrect
A . No matching user account exists for this user
Incorrect.
If the user account did not exist, the login page would still appear, but authentication would fail after credentials are entered.
B . The Remote-users group must be set up correctly in the FSSO configuration
Incorrect.
This policy is using active authentication, not FSSO.
FSSO configuration is irrelevant for active authentication login prompts.
C . The Remote-users group is not added to the Destination
Incorrect.
User groups are applied in the Source field for authentication-based policies.
Destination does not accept user groups.
When configuring firewall policies which of the following is true regarding the policy ID? (Choose two.)
According to the FortiOS 7.6 Firewall Policy administration documentation, the correct answers are A and B.
Analysis of Each Statement
A . A firewall policy ID identifies the order of policy execution in firewall policies.
Correct
In FortiOS, each firewall policy is assigned a policy ID, which is used internally to reference the policy.
Policies are evaluated top-down, and the policy ID reflects the relative order in which the policy exists in the policy table.
While the GUI shows policies by sequence, that sequence is tied to the policy ID ordering.
Fortinet documentation and study guides commonly describe the policy ID as identifying the policy's execution order.
Therefore, this statement is considered true in the context of FortiOS administration and certification exams.
B . A policy ID cannot be modified once a policy is created.
Correct
Once a firewall policy is created, its policy ID is fixed.
You can:
Move the policy up or down in the policy list
Edit the policy contents
But you cannot change the policy ID itself.
This is explicitly documented behavior in FortiOS.
C . You can create a policy in CLI with policy ID 0
Incorrect
Policy ID 0 is reserved by FortiOS.
In the CLI, using:
edit 0
does not create a policy with ID 0; instead, it tells FortiGate to automatically assign the next available policy ID.
A real firewall policy with ID 0 cannot exist.
D . It is mandatory to provide a policy ID while creating a firewall policy regardless of GUI or CLI.
Incorrect
In the GUI, policy IDs are assigned automatically.
In the CLI, administrators can use edit 0 to auto-generate a policy ID.
Therefore, manually specifying a policy ID is not mandatory.