At ValidExamDumps, we consistently monitor updates to the Fortinet FCSS_SASE_AD-24 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet FCSS - FortiSASE 24 Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet FCSS_SASE_AD-24 exam. These outdated questions lead to customers failing their Fortinet FCSS - FortiSASE 24 Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet FCSS_SASE_AD-24 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little dat
a. What is a possible explanation for this almost empty report?
If the daily summary report generated by FortiSASE contains very little data, one possible explanation is that the 'Log allowed traffic' setting is configured to log only 'Security Events' for all policies. This configuration limits the amount of data logged, as it only includes security events and excludes normal allowed traffic.
Log Allowed Traffic Setting:
The 'Log allowed traffic' setting determines which types of traffic are logged.
When set to 'Security Events,' only traffic that triggers a security event (such as a threat detection or policy violation) is logged.
Impact on Report Data:
If the log setting excludes regular allowed traffic, the amount of data captured and reported is significantly reduced.
This results in reports with minimal data, as only security-related events are included.
FortiOS 7.2 Administration Guide: Provides details on configuring logging settings for traffic policies.
FortiSASE 23.2 Documentation: Explains the impact of logging configurations on report generation and data visibility.
Refer to the exhibits.
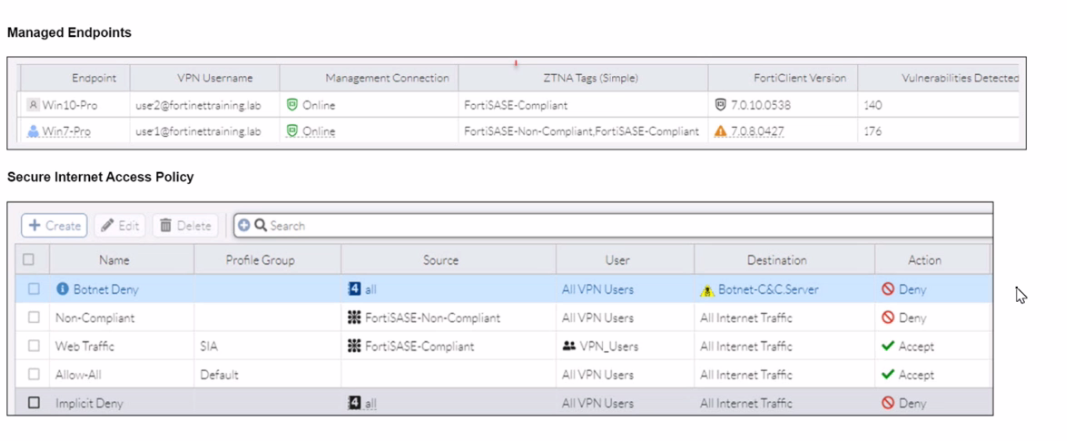
WiMO-Pro and Win7-Pro are endpoints from the same remote location. WiMO-Pro can access the internet though FortiSASE, while Wm7-Pro can no longer access the internet
Given the exhibits, which reason explains the outage on Wm7-Pro?
Based on the provided exhibits, the reason why the Win7-Pro endpoint can no longer access the internet through FortiSASE is due to exceeding the total vulnerability detected threshold. This threshold is used to determine if a device is compliant with the security requirements to access the network.
Endpoint Compliance:
FortiSASE monitors endpoint compliance by assessing various security parameters, including the number of vulnerabilities detected on the device.
The compliance status is indicated by the ZTNA tags and the vulnerabilities detected.
Vulnerability Threshold:
The exhibit shows that Win7-Pro has 176 vulnerabilities detected, whereas Win10-Pro has 140 vulnerabilities.
If the endpoint exceeds a predefined vulnerability threshold, it may be restricted from accessing the network to ensure overall network security.
Impact on Network Access:
Since Win7-Pro has exceeded the vulnerability threshold, it is marked as non-compliant and subsequently loses internet access through FortiSASE.
The FortiSASE endpoint profile enforces this compliance check to prevent potentially vulnerable devices from accessing the internet.
FortiOS 7.2 Administration Guide: Provides information on endpoint compliance and vulnerability management.
FortiSASE 23.2 Documentation: Explains how vulnerability thresholds are used to determine endpoint compliance and access control.
When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
When configuring FortiSASE Secure Private Access (SPA) with SD-WAN integration, establishing a routing adjacency between FortiSASE and the FortiGate SD-WAN hub requires the use of the Border Gateway Protocol (BGP).
BGP (Border Gateway Protocol):
BGP is widely used for establishing routing adjacencies between different networks, particularly in SD-WAN environments.
It provides scalability and flexibility in managing dynamic routing between FortiSASE and the FortiGate SD-WAN hub.
Routing Adjacency:
BGP enables the exchange of routing information between FortiSASE and the FortiGate SD-WAN hub.
This ensures optimal routing paths and efficient traffic management across the hybrid network.
FortiOS 7.2 Administration Guide: Provides information on configuring BGP for SD-WAN integration.
FortiSASE 23.2 Documentation: Details on setting up routing adjacencies using BGP for Secure Private Access with SD-WAN.
Refer to the exhibits.
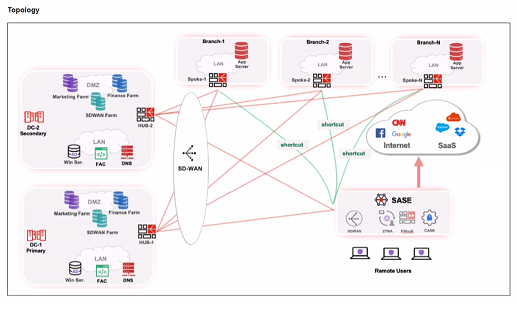
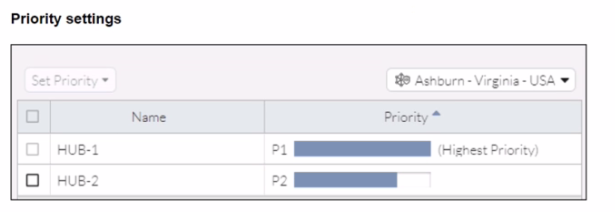
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
Refer to the exhibits.
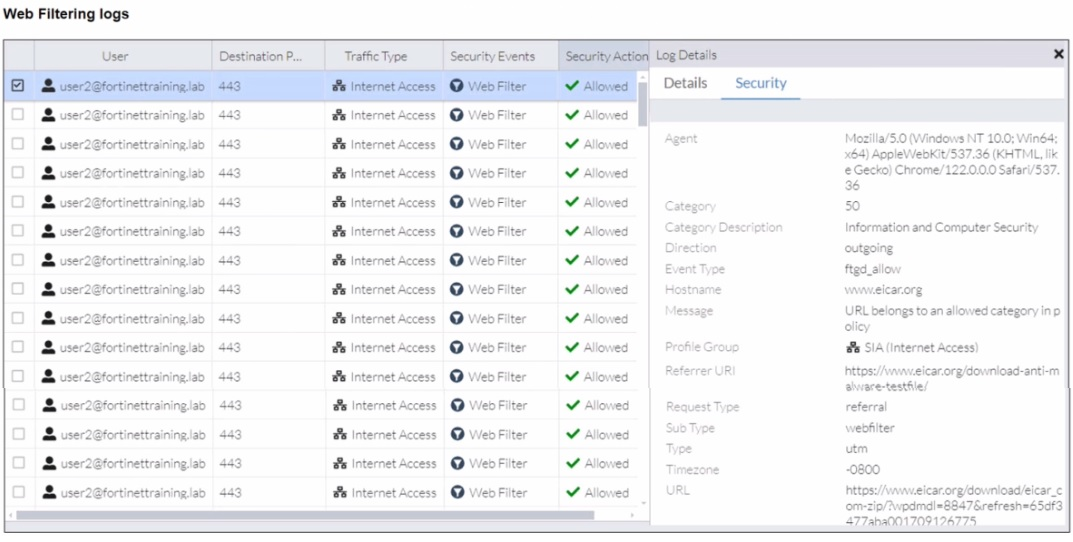
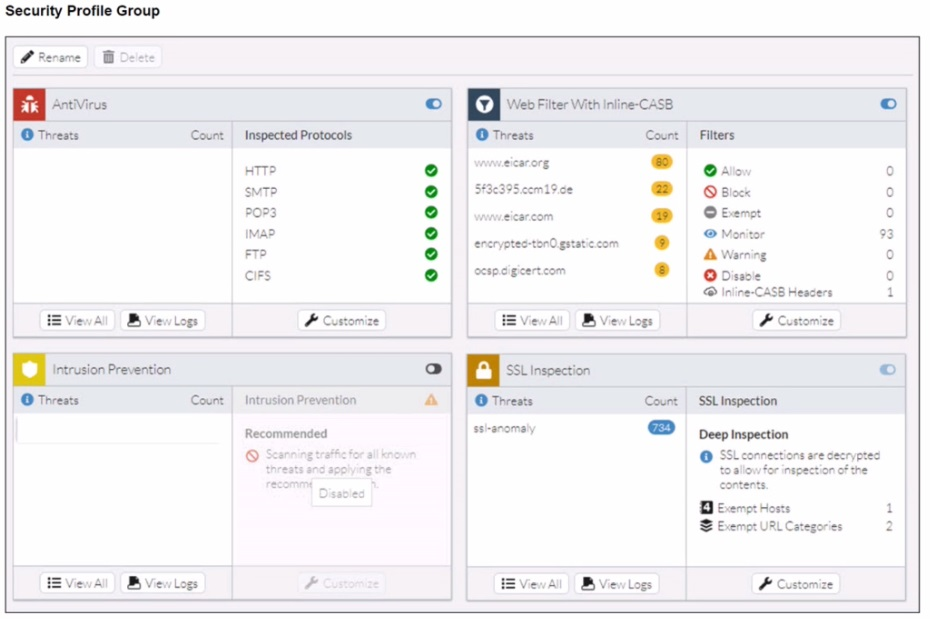
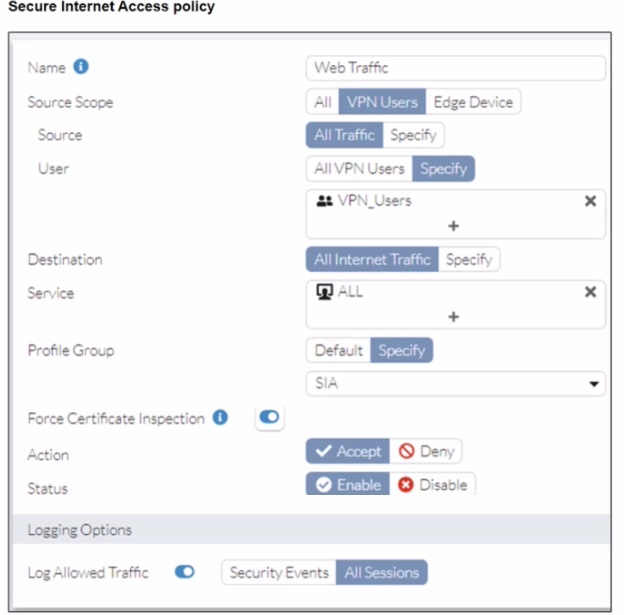
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org. Traffic logs show traffic is allowed by the policy.
Which configuration on FortiSASE is allowing users to perform the download?