At ValidExamDumps, we consistently monitor updates to the Fortinet FCSS_SASE_AD-23 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet FCSS - FortiSASE 23 Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet FCSS_SASE_AD-23 exam. These outdated questions lead to customers failing their Fortinet FCSS - FortiSASE 23 Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet FCSS_SASE_AD-23 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibits.
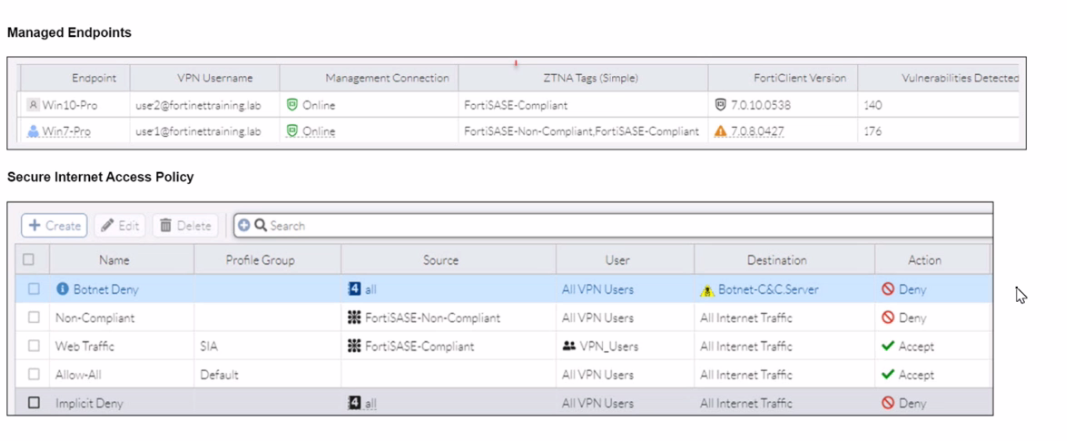
WiMO-Pro and Win7-Pro are endpoints from the same remote location. WiMO-Pro can access the internet though FortiSASE, while Wm7-Pro can no longer access the internet
Given the exhibits, which reason explains the outage on Wm7-Pro?
Based on the provided exhibits, the reason why the Win7-Pro endpoint can no longer access the internet through FortiSASE is due to exceeding the total vulnerability detected threshold. This threshold is used to determine if a device is compliant with the security requirements to access the network.
Endpoint Compliance:
FortiSASE monitors endpoint compliance by assessing various security parameters, including the number of vulnerabilities detected on the device.
The compliance status is indicated by the ZTNA tags and the vulnerabilities detected.
Vulnerability Threshold:
The exhibit shows that Win7-Pro has 176 vulnerabilities detected, whereas Win10-Pro has 140 vulnerabilities.
If the endpoint exceeds a predefined vulnerability threshold, it may be restricted from accessing the network to ensure overall network security.
Impact on Network Access:
Since Win7-Pro has exceeded the vulnerability threshold, it is marked as non-compliant and subsequently loses internet access through FortiSASE.
The FortiSASE endpoint profile enforces this compliance check to prevent potentially vulnerable devices from accessing the internet.
FortiOS 7.2 Administration Guide: Provides information on endpoint compliance and vulnerability management.
FortiSASE 23.2 Documentation: Explains how vulnerability thresholds are used to determine endpoint compliance and access control.
Which two deployment methods are used to connect a FortiExtender as a FortiSASE LAN extension? (Choose two.)
There are two deployment methods used to connect a FortiExtender as a FortiSASE LAN extension:
Connect FortiExtender to FortiSASE using FortiZTP:
FortiZero Touch Provisioning (FortiZTP) simplifies the deployment process by allowing FortiExtender to automatically connect and configure itself with FortiSASE.
This method requires minimal manual configuration, making it efficient for large-scale deployments.
Enter the FortiSASE domain name in the FortiExtender GUI as a static discovery server:
Manually configuring the FortiSASE domain name in the FortiExtender GUI allows the extender to discover and connect to the FortiSASE infrastructure.
This static discovery method ensures that FortiExtender can establish a connection with FortiSASE using the provided domain name.
FortiOS 7.2 Administration Guide: Details on FortiExtender deployment methods and configurations.
FortiSASE 23.2 Documentation: Explains how to connect and configure FortiExtender with FortiSASE using FortiZTP and static discovery.
You are designing a new network for Company X and one of the new cybersecurity policy requirements is that all remote user endpoints must always be connected and protected Which FortiSASE component facilitates this always-on security measure?
The unified FortiClient component of FortiSASE facilitates the always-on security measure required for ensuring that all remote user endpoints are always connected and protected.
Unified FortiClient:
FortiClient is a comprehensive endpoint security solution that integrates with FortiSASE to provide continuous protection for remote user endpoints.
It ensures that endpoints are always connected to the FortiSASE infrastructure, even when users are off the corporate network.
Always-On Security:
The unified FortiClient maintains a persistent connection to FortiSASE, enforcing security policies and protecting endpoints against threats at all times.
This ensures compliance with the cybersecurity policy requiring constant connectivity and protection for remote users.
FortiOS 7.2 Administration Guide: Provides information on configuring and managing FortiClient for endpoint security.
FortiSASE 23.2 Documentation: Explains how FortiClient integrates with FortiSASE to deliver always-on security for remote endpoints.
A customer wants to upgrade their legacy on-premises proxy to a could-based proxy for a hybrid network. Which FortiSASE features would help the customer to achieve this outcome?
For a customer looking to upgrade their legacy on-premises proxy to a cloud-based proxy for a hybrid network, the combination of Secure Web Gateway (SWG) and Inline Cloud Access Security Broker (CASB) features in FortiSASE will provide the necessary capabilities.
Secure Web Gateway (SWG):
SWG provides comprehensive web security by inspecting and filtering web traffic to protect against web-based threats.
It ensures that all web traffic, whether originating from on-premises or remote locations, is inspected and secured by the cloud-based proxy.
Inline Cloud Access Security Broker (CASB):
CASB enhances security by providing visibility and control over cloud applications and services.
Inline CASB integrates with SWG to enforce security policies for cloud application usage, preventing unauthorized access and data leakage.
FortiOS 7.2 Administration Guide: Details on SWG and CASB features.
FortiSASE 23.2 Documentation: Explains how SWG and inline-CASB are used in cloud-based proxy solutions.
Which policy type is used to control traffic between the FortiClient endpoint to FortiSASE for secure internet access?
The Secure Web Gateway (SWG) policy is used to control traffic between the FortiClient endpoint and FortiSASE for secure internet access. SWG provides comprehensive web security by enforcing policies that manage and monitor user access to the internet.
Secure Web Gateway (SWG) Policy:
SWG policies are designed to protect users from web-based threats and enforce acceptable use policies.
These policies control and monitor user traffic to and from the internet, ensuring that security protocols are followed.
Traffic Control:
The SWG policy intercepts all web traffic, inspects it, and applies security rules before allowing or blocking access.
This policy type is crucial for providing secure internet access to users connecting through FortiSASE.
FortiOS 7.2 Administration Guide: Details on configuring and managing SWG policies.
FortiSASE 23.2 Documentation: Explains the role of SWG in securing internet access for endpoints.