At ValidExamDumps, we consistently monitor updates to the Fortinet FCP_WCS_AD-7.4 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet FCP - AWS Cloud Security 7.4 Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet FCP_WCS_AD-7.4 exam. These outdated questions lead to customers failing their Fortinet FCP - AWS Cloud Security 7.4 Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet FCP_WCS_AD-7.4 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.
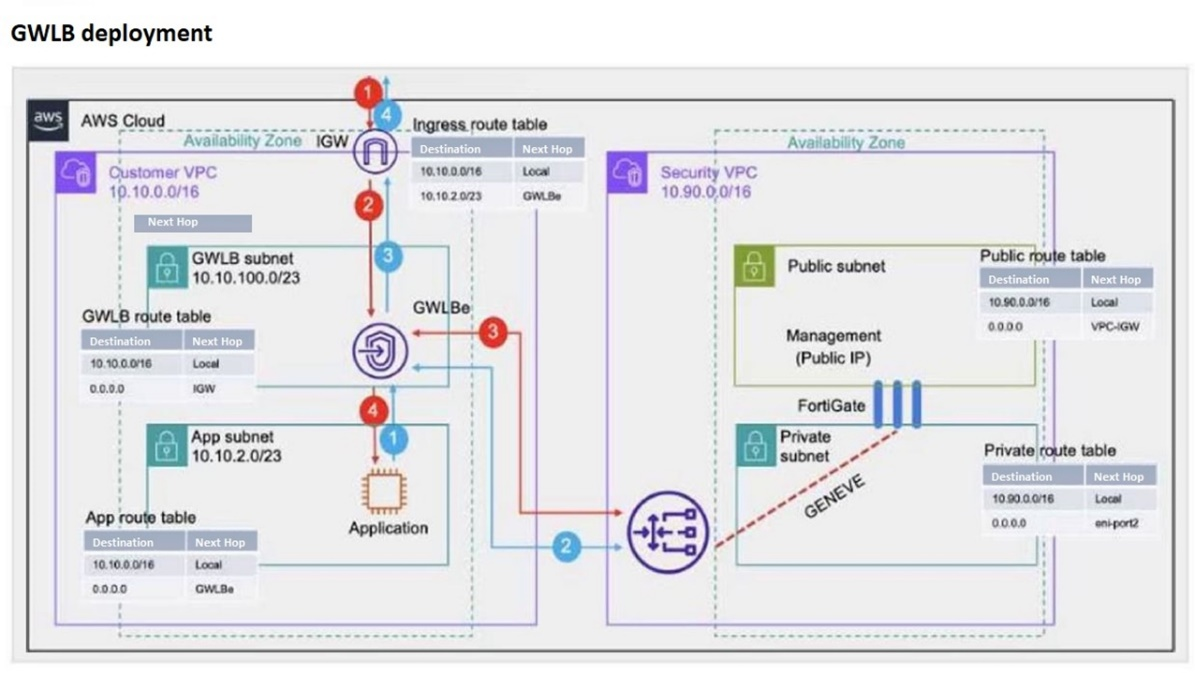
Which two statements are true about inbound traffic based on the IGW ingress route table and GWLB deployment shown in the exhibit? (Choose two.)
Traffic Direction through GWLB Endpoint:
The ingress route table directs inbound traffic to the GWLB through a GWLB endpoint (GWLBe). This endpoint is responsible for directing traffic to the Gateway Load Balancer for further processing (Option B).
GENEVE Encapsulation:
The GWLB encapsulates the inbound traffic using the GENEVE protocol. This encapsulated traffic is then sent to FortiGate instances for security inspection. The use of GENEVE ensures that the original traffic context is preserved and can be analyzed by FortiGate (Option D).
Other Options Analysis:
Option A is incorrect because GWLB does not forward traffic without encapsulation in its dedicated subnet.
Option C is incorrect as the inbound traffic is directed to the GWLB endpoint first, not directly to the application subnet.
AWS Gateway Load Balancer Documentation: AWS GWLB
GENEVE Protocol Overview: GENEVE Protocol
Refer to the exhibit.
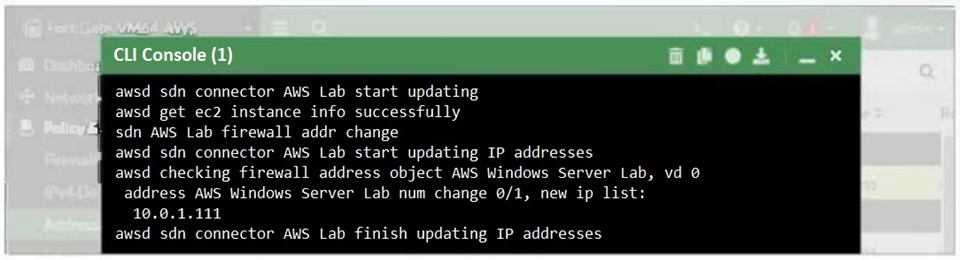
What two conclusions can you draw from the FortiGate debug output? (Choose two.)
Dynamic Address Object Update:
The debug output shows that the IP address of the AWS Windows Server Lab has been updated automatically, indicating that the dynamic address object feature is working as intended. This allows FortiGate to adapt to changes in the IP addresses of AWS instances dynamically (Option A).
SDN Connector Configuration:
The messages in the debug output confirm that the SDN connector is able to retrieve instance information and update the firewall address objects successfully. This implies that the SDN connector is correctly configured and has the necessary permissions (Option C).
Manual Change and Permissions:
Option B is incorrect because while the address object could theoretically be changed manually, this is not inferred from the debug output.
Option D is incorrect because the debug output does not indicate that the AWS user account must have full administrative rights. The required permissions are typically more scoped to specific actions related to SDN.
FortiGate AWS Integration Guide: FortiGate on AWS
A customer has deployed FortiGate Cloud-Native Firewall (CNF).
Which two statements are correct about policy sets? (Choose two.)
Implicit Deny Rule:
Similar to traditional firewall rule sets, FortiGate Cloud-Native Firewall (CNF) includes an implicit deny rule at the bottom of each policy set. This means any traffic that does not match an existing rule in the policy set is automatically denied (Option A).
Policy Set Creation:
When a new CNF instance is deployed, a new policy set is created specifically for that instance. This ensures that each CNF instance can have a tailored set of security policies based on the specific needs of the deployment (Option C).
Other Options Analysis:
Option B is incorrect because policy sets do not require manual synchronization; they are applied automatically once configured.
Option D is incorrect as a single CNF instance operates with a single policy set at a time.
FortiGate CNF Documentation: FortiGate CNF
Firewall Policy Best Practices: Fortinet Policies
Your customers have been reporting slow response times when accessing your web application.
What are two possible ways to increase response times from web servers protected by FortiWeb Cloud? (Choose two.)
Your customers have been reporting slow response times when accessing your web application.
What are two possible ways to increase response times from web servers protected by FortiWeb Cloud? (Choose two.)
Same Region Deployment:
Deploying FortiWeb Cloud in the same AWS region as your web application minimizes latency and ensures faster response times by reducing the distance data needs to travel (Option A).
Content Delivery Network (CDN):
Enabling a CDN can significantly improve response times by caching content closer to the end-users, reducing the load on the origin server, and speeding up content delivery (Option B).
Other Options Analysis:
Option C is incorrect because modifying DNS entries to directly point to your web server bypasses the WAF protection, which is not advisable for security reasons.
Option D is incorrect because disabling WAF functionality would expose your web application to vulnerabilities and threats, compromising security.
Your company deployed a FortiSandbox for AWS.
Which statement is correct about FortiSandbox for AWS?
FortiSandbox Deployment:
FortiSandbox for AWS deploys new EC2 instances to create isolated environments where it can safely execute and analyze suspicious files. These instances run custom Windows and Linux virtual machines specifically configured for sandboxing (Option D).
Sandboxing Process:
The process involves sending potential malware to these isolated VMs, executing it, and monitoring its behavior to detect malicious activities. The results are then captured and analyzed to provide detailed threat intelligence.
Other Options Analysis:
Option A is incorrect because FortiSandbox for AWS operates entirely within the AWS environment and does not require an on-premises manager.
Option B is incorrect as the FortiSandbox manager is not installed on the AWS platform for managing on-premises instances.
Option C is incorrect because FortiSandbox requires sufficient resources to perform the actual sandboxing and analysis tasks.
FortiSandbox for AWS Documentation: FortiSandbox