At ValidExamDumps, we consistently monitor updates to the Fortinet FCP_FWB_AD-7.4 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet FCP - FortiWeb 7.4 Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet FCP_FWB_AD-7.4 exam. These outdated questions lead to customers failing their Fortinet FCP - FortiWeb 7.4 Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet FCP_FWB_AD-7.4 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Which two functions does the first layer of the FortiWeb anomaly machine learning (ML) analysis mechanism perform? (Choose two.)
The first layer of the FortiWeb anomaly machine learning (ML) analysis mechanism focuses on analyzing traffic and creating a probability model for parameters and HTTP methods to detect potential anomalies. It also assesses traffic patterns over time to determine whether certain behavior is anomalous. These functions are key to understanding and classifying traffic before further analysis is done.
An attacker attempts to send an SQL injection attack containing the known attack string 'root'; -- through an API call.
Which FortiWeb inspection feature will be able to detect this attack the quickest?
The quickest detection for an SQL injection attack like the one described ('root'; --) would be through known signatures. FortiWeb utilizes signature-based detection to match incoming traffic against predefined attack patterns. Since SQL injection attacks are commonly known and have specific patterns (such as 'root'; --), known signatures would immediately recognize and flag this type of attack.
You are using HTTP content routing on FortiWeb. You want requests for web application A to be forwarded to a cluster of web servers, which all host the same web application. You want requests for web application B to be forwarded to a different, single web server.
Which statement regarding this solution is true?
To forward requests for web application B to a single web server, you would configure FortiWeb to use HTTP content routing and create a server pool specifically for web application B. In FortiWeb, server pools are used to group servers together based on application requirements, and you can configure the pool to contain only a single web server for application B.
Refer to the exhibit.
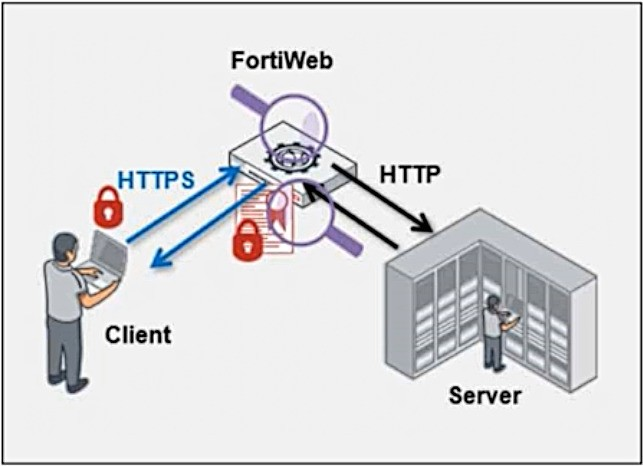
Which statement is true?
In the diagram, FortiWeb is positioned between the client and the server, handling encrypted HTTPS traffic from the client and sending unencrypted HTTP traffic to the server. This indicates that FortiWeb is performing SSL offloading, which means it is decrypting the HTTPS traffic from the client, inspecting it, and then re-encrypting the traffic before forwarding it to the server.
Refer to the exhibit.
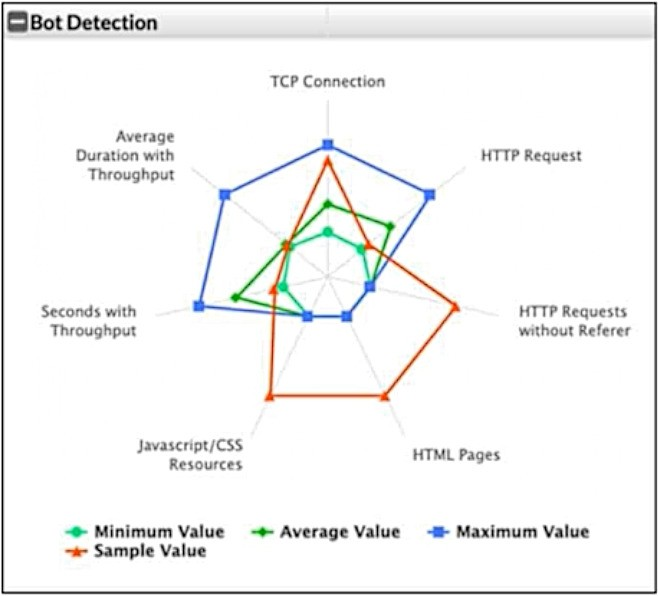
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?
In the SVM plot of potential bot activity, you can see that the sample value (orange) is significantly different from the average value (green) and the maximum value (blue) in most of the metrics. This suggests unusual or abnormal behavior, indicating that the connection might be a bot. Typically, bots exhibit patterns that diverge from normal user activity, such as higher frequencies of certain types of requests, abnormal throughput, or an unusual pattern of HTTP requests (such as requests without referers or excessive TCP connections).