At ValidExamDumps, we consistently monitor updates to the Fortinet FCP_FCT_AD-7.2 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet FCP - FortiClient EMS 7.2 Administrator exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet FCP_FCT_AD-7.2 exam. These outdated questions lead to customers failing their Fortinet FCP - FortiClient EMS 7.2 Administrator exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet FCP_FCT_AD-7.2 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
An administrator wants to simplify remote access without asking users to provide user credentials Which access control method provides this solution?
Simplifying Remote Access:
The administrator wants to simplify remote access without asking users to provide user credentials.
Evaluating Access Control Methods:
ZTNA full mode can provide seamless access by leveraging device identity and posture, eliminating the need for user credentials for each access request.
Other methods like SSL VPN and L2TP typically require user credentials.
Conclusion:
The correct access control method that provides this solution is ZTNA full mode.
ZTNA section in the FortiGate Infrastructure 7.2 Study Guide.
Refer to the exhibits.
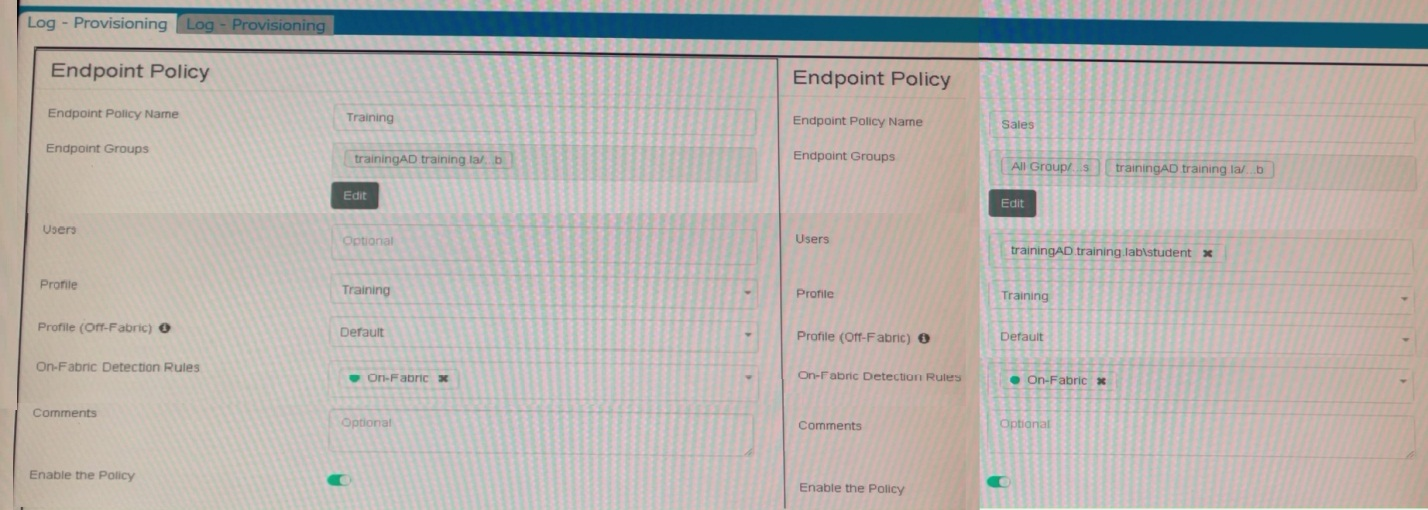
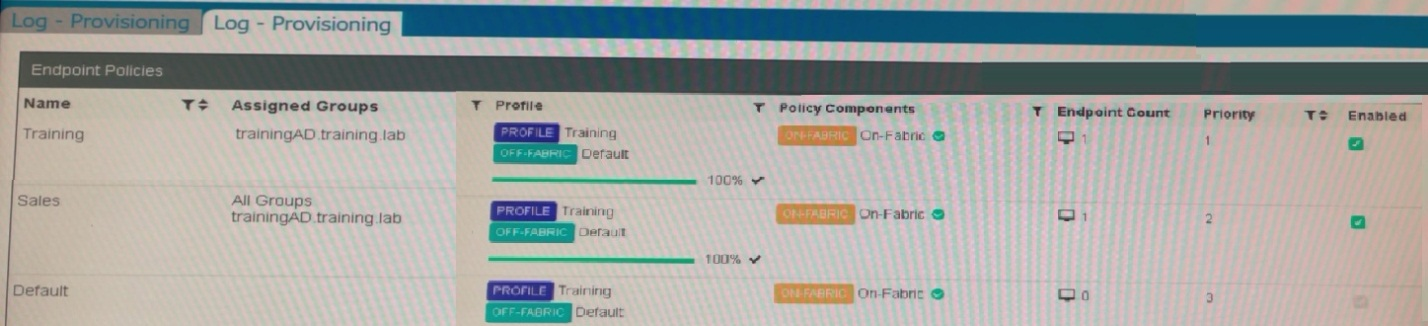
Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account student on an endpoint in the trainingAD domain?
Based on the configuration shown in the exhibits:
There are three endpoint policies configured: Training, Sales, and Default.
The 'Training' policy is assigned to the 'trainingAD.training.lab' group.
The 'Sales' policy is assigned to 'All Groups' and 'trainingAD.training.lab/student.'
The 'Default' policy has no specific groups assigned.
When someone logs in with the user account 'student' on an endpoint in the 'trainingAD' domain:
The 'Training' policy is specifically assigned to the 'trainingAD.training.lab' group.
The 'Sales' policy includes 'trainingAD.training.lab/student' but not the general 'trainingAD.training.lab' group.
The system will prioritize the most specific match for the group.
Therefore, FortiClient EMS will assign the 'Training' policy to the 'student' account logging into the 'trainingAD' domain as it matches the group 'trainingAD.training.lab' directly.
Reference
FortiClient EMS 7.2 Study Guide, Endpoint Policy Configuration Section
FortiClient EMS Documentation on Group Policy Assignment and Matching
Which component or device shares ZTNA tag information through Security Fabric integration?
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
Administrators can use several third-party tools to deploy FortiClient:
Microsoft SCCM (System Center Configuration Manager): SCCM is a robust tool used for deploying software across large numbers of Windows-based systems. It supports deployment of FortiClient through its software distribution capabilities.
Microsoft Active Directory GPO (Group Policy Object): GPOs are used to manage user and computer settings in an Active Directory environment. Administrators can deploy FortiClient to multiple machines using GPO software installation settings.
These tools provide centralized and scalable methods for deploying FortiClient across numerous endpoints in an enterprise environment.
Reference
FortiClient EMS 7.2 Study Guide, FortiClient Deployment Section
Fortinet Documentation on FortiClient Deployment using SCCM and GPO
When site categories are disabled in FortiClient web filter, which feature can be used to protect the endpoint from malicious web access?
Web Filter Functionality:
When site categories are disabled in the FortiClient web filter, the endpoint still requires protection from malicious web access.
Alternative Protection Features:
The web exclusion list can be used to manage and block specific URLs that are known to be malicious, providing a way to control and secure web access even without site categories being enabled.
Conclusion:
The correct feature that can be used to protect the endpoint in this scenario is the web exclusion list (D).
FortiClient web filter configuration and features from the study guides.