At ValidExamDumps, we consistently monitor updates to the F5 Networks 201 exam questions by F5 Networks. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the F5 Networks TMOS Administration exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by F5 Networks in their F5 Networks 201 exam. These outdated questions lead to customers failing their F5 Networks TMOS Administration exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the F5 Networks 201 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.
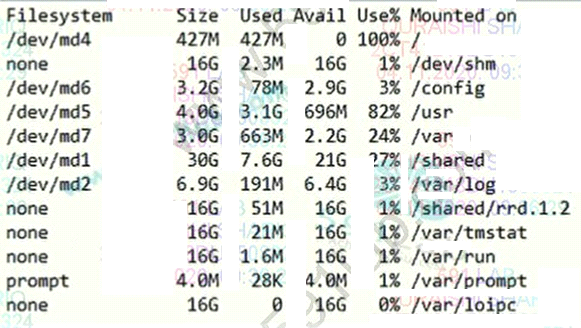
The BIG-IP Administrator is investigating disk utilization on the BIG-IP device.
What should the BIG-IP Administrator check next?
A BIG-IP has a virtual server at 150.150.10.10:80 with SNAT automap configured. This BIG-IP also has a SNAT at 150.150.10.11 set for a source address range of 200.200.1.0 / 255.255.255.0. All other settings are at
their default states. If a client with the IP address 200.200.1.1 sends a request to the virtual server, what is the source IP address when the associated packet is sent to the pool member?
Active connections to pool members are unevenly distributed. The load balancing method is Least Connections (member) Priority Group Activation is disabled. What is a potential cause of the event distribution?
How should a BIG-IP Administrator persistent sessions from being sent to a pool member so that the server administrator can perform maintenance?