At ValidExamDumps, we consistently monitor updates to the Cisco 350-701 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Implementing and Operating Cisco Security Core Technologies exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 350-701 exam. These outdated questions lead to customers failing their Cisco Implementing and Operating Cisco Security Core Technologies exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 350-701 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
[Secure Network Access, Visibility, and Enforcement]
Which RADIUS feature provides a mechanism to change the AAA attributes of a session after it is
authenticated?
CoA stands for Change of Authorization, which is a feature that allows a RADIUS server to adjust an active client session after it is authenticated. For example, CoA can be used to reauthenticate a client, terminate a client session, or change the VLAN or group policy of a client. CoA is supported by several RADIUS vendors, including Cisco ISE. CoA is defined in RFC 5176 and uses a pushed model, where the request originates from the RADIUS server and is sent to the network device that acts as a listener. CoA requests can have two possible response codes: CoA-ACK (acknowledgment) or CoA-NAK (non-acknowledgment).Reference:=
Some possible references are:
RADIUS Change of Authorization
Change of Authorization with RADIUS (CoA) on MR Access Points
Change of Authorization with RADIUS (CoA) on MS Switches
Technical Tip: Radius COA behavior
[Content Security]
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the
corporate network. The endpoints must have the corporate antivirus application installed and be running the
latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the
network?
Cisco Identity Services Engine (ISE) and AnyConnect Posture module are the best solution to ensure that all endpoints are compliant before users are allowed access on the corporate network. ISE is a policy-based platform that provides secure network access, identity management, and endpoint compliance. AnyConnect Posture module is a component of the AnyConnect Secure Mobility Client that performs posture assessment and remediation on the endpoints. Together, they can enforce policies based on the endpoint's compliance status, such as the presence and update of the corporate antivirus application and the Windows 10 build version. The administrator can configure posture requirements, profiles, and policies on ISE, and deploy them to the endpoints through AnyConnect. The endpoints will then report their posture status to ISE, which will grant or deny network access accordingly, or redirect them to a remediation portal if needed.Reference:
[Network Security]
A network administrator is modifying a remote access VPN on an FTD managed by an FMC. The administrator wants to offload traffic to certain trusted domains. The administrator wants this traffic to go out of the client's local internet and send other internet-bound traffic over the VPN Which feature must the administrator configure?
In a remote access VPN configuration, dynamic split tunneling allows traffic to certain trusted domains to bypass the VPN tunnel and exit through the client's local internet gateway. This feature selectively directs only the necessary traffic over the VPN, while allowing direct internet access for specific domains or traffic deemed safe or trusted, optimizing bandwidth and performance for remote users.
[Security Concepts]
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
The Talos IP and Domain Reputation Center is the world's most comprehensive real-time threat detection network. It collects and analyzes data from millions of web requests, emails, malware samples, open-source data sets, endpoint intelligence, and network intrusions. It assigns a reputation score to IP addresses and domains based on their observed malicious activity and behavior. The reputation score can range from -10 (very malicious) to +10 (very benign). The reputation score can be used to block or allow traffic, or to trigger further inspection or analysis. The Talos IP and Domain Reputation Center allows you to track the reputation of IP addresses for email and web traffic, as well as to look up the category, volume, and history of any IP address or domain. You can also submit feedback or request a change of reputation for any IP address or domain.Reference
https://talosintelligence.com/reputation_center/
https://bing.com/search?q=Talos+reputation+center+IP+addresses+email+web+traffic
[Security Concepts]
Refer to the exhibit.
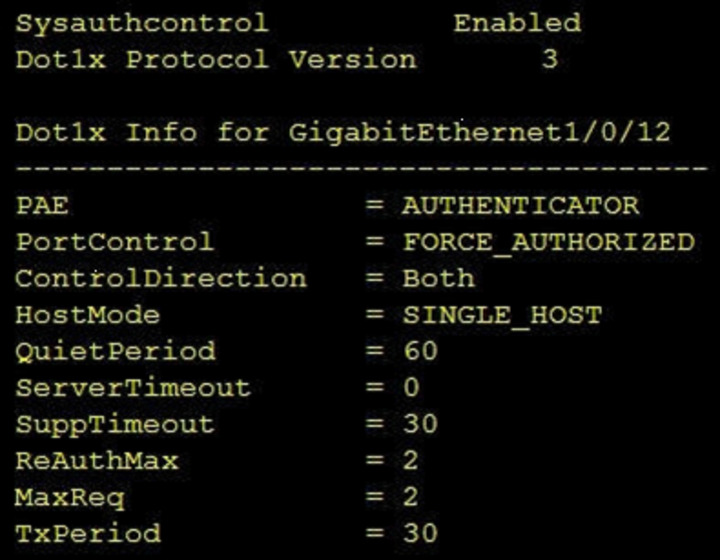
Which command was used to display this output?
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3850/sec-user-8021x-xe-3se-3850-book/config-ieee-802x-pba.html