At ValidExamDumps, we consistently monitor updates to the Cisco 300-740 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Designing and Implementing Secure Cloud Access for Users and Endpoints exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 300-740 exam. These outdated questions lead to customers failing their Cisco Designing and Implementing Secure Cloud Access for Users and Endpoints exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 300-740 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.
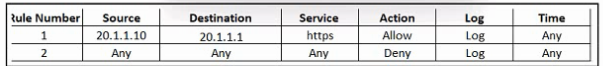
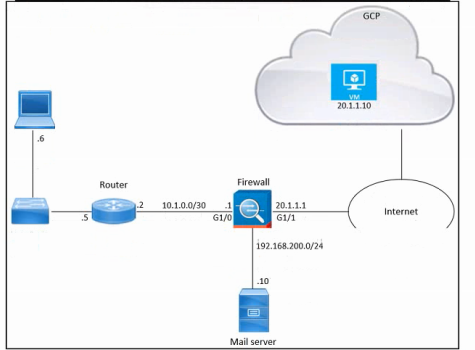
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
Refer to the exhibit.
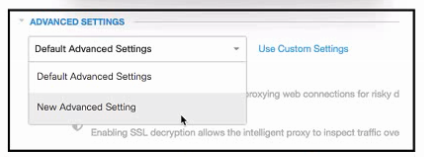
Refer to the exhibit. An engineer must configure a global allow list in Cisco Umbrella for the cisco.com domain. All other domains must be blocked. After creating a new policy and adding the cisco.com domain, the engineer attempts to access a site outside of cisco.com and is successful. Which additional Security Settings action must be taken to meet the requirement?
Refer to the exhibit.
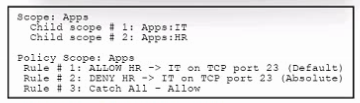
Refer to the exhibit. An engineer must analyze a segmentation policy in Cisco Secure Workload. What is the result of applying the policy?
Which common strategy should be used to mitigate directory traversal attacks in a cloud environment?