At ValidExamDumps, we consistently monitor updates to the Cisco 300-540 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Designing and Implementing Cisco Service Provider Cloud Network Infrastructure v1.0 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 300-540 exam. These outdated questions lead to customers failing their Cisco Designing and Implementing Cisco Service Provider Cloud Network Infrastructure v1.0 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 300-540 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.

Refer to the exhibit. An engineer must configure an IPsec VPN connection between site 1 and site 2. The ISAKMP policy for the phase 1 negotiations of the tunnel must use AES and SHA-256. This configuration was applied to both PE routers; however, the tunnel fails to come up:
crypto isakmp policy 10
encryption 3des
hash md5
authentication pre-share
group 12
Which two commands must be run on router PE1 to resolve the issue? (Choose two.)
Phase 1 of an IPsec tunnel (ISAKMP/IKE) must have matching proposals on both peers for:
Encryption algorithm
Hash (integrity) algorithm
Authentication method
DH group
The requirement states that AES and SHA-256 must be used. The current configuration uses:
encryption 3des incorrect (must be AES)
hash md5 incorrect (must be SHA-256)
To meet the requirement, we must modify the ISAKMP policy:
crypto isakmp policy 10
encryption aes change 3DES to AES
hash sha256 change MD5 to SHA-256
authentication pre-share
group 12
Therefore, the necessary commands on PE1 are:
encryption aes option B
hash sha256 option E
Options C and D are invalid syntax (encryption sha256 and hash aes are not supported). Changing the DH group (A) is not required by the problem statement and would not by itself fix the mismatch related to encryption and hash algorithms.
Refer to the exhibit.


Refer to the exhibit. An engineer is troubleshooting an issue where Cisco switch Switch_A fails to establish OTV connectivity to Cisco switch Switch_C. What is the cause of the issue?
A. The broadcast group must be 232.1.1.0. B. The join interface must be g1/0. C. The control group must be 232.1.1.0. D. The join interface must be e1/1.
In Cisco Overlay Transport Virtualization (OTV), the join interface is the Layer 3 interface that connects the edge device to the transport network (the routed core / WAN) where multicast groups (control, data, broadcast) are reachable.
From the topology:
Interface g1/0 on Switch_A is connected to the routed 20.20.20.0/30 link toward Switch_C (the transport / WAN).
Interface g1/1 is a trunk toward Switch_B and carries extended VLANs (101, 111), so it belongs to the internal site-facing side, not the transport.
In the show otv output, the join interface is incorrectly configured as g1/1 (20.20.20.2), which is an internal trunk and not the correct routed interface to the OTV transport network. Because the join interface does not face the multicast-enabled transport, OTV cannot establish adjacency and the VPN state remains DOWN.
Correct configuration should use:
otv join-interface GigabitEthernet1/0
Options A and C about group addresses are not the issue; addresses shown (224.x for control/broadcast and 232.x for data group range) are valid multicast ranges. Option D (e1/1) is also an internal access/trunk interface and not the WAN transport interface.
Refer to the exhibit.
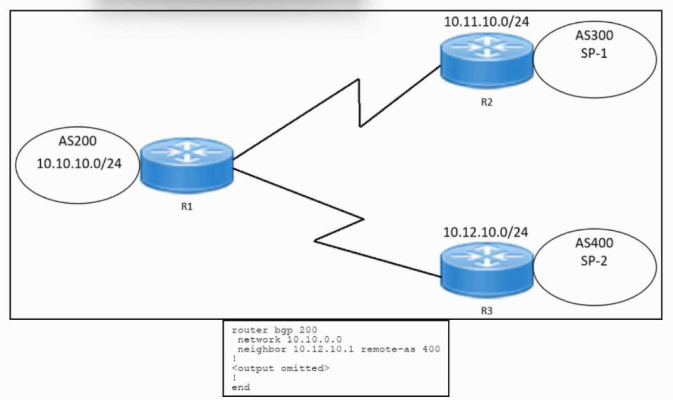
Refer to the exhibit. An engineer must configure multihoming between router R1 and service provider SP-2. Locally generated routes must be advertised to service provider SP-2. Which command must be run on R1 to complete the configuration?
A. network 10.0.0.0 route-map as200only out B. neighbor 10.12.10.1 route-map localonly out C. network 10.12.10.1 route-map as200only in D. neighbor 10.0.0.0 route-map localonly out
On R1 (AS200), the requirement is:
Advertise locally generated routes (for example, 10.10.10.0/24 from AS200)
Only toward SP-2, which peers on IP 10.12.10.1
Apply a policy (route-map) controlling what R1 advertises
In BGP, to control which locally originated routes are sent to a specific neighbor, the correct configuration is:
neighbor <IP> route-map <map-name> out
This applies outbound policy filtering or permitting to the prefixes advertised.
Thus:
The neighbor toward SP-2 is 10.12.10.1
The route-map must be applied outbound
The command that accomplishes this is:
neighbor 10.12.10.1 route-map localonly out
Why the Other Options Are Incorrect
A . network 10.0.0.0 route-map as200only out The network command does not accept route-map out. This is invalid syntax.
C . network 10.12.10.1 route-map as200only in Incorrect network, incorrect direction, and invalid syntax with in.
D . neighbor 10.0.0.0 route-map localonly out 10.0.0.0 is not a BGP neighbor; it's a network prefix.
How does log management assist in meeting the requirements of cloud security regulatory compliance?
Comprehensive and Detailed Explanation From Cisco SP Cloud Network Infrastructure Security Knowledge
Cloud security compliance frameworks (such as ISO 27001, PCI-DSS, GDPR, SOC 2, HIPAA) require:
Evidence of security events
Retention of logs for audit periods
Ability to generate compliance reports
Traceability and accountability
Incident investigation support
Effective log management enables:
Centralized collection of application, network, and system logs
Storage of logs for mandated retention periods
Generation of audit-ready reports
Documentation required for compliance assessments
Demonstration that monitoring and security controls are active and functioning
Therefore, the role of log management in regulatory compliance is primarily about documentation, traceability, auditing, and reporting, which aligns only with Option A.
The other options do not directly serve regulatory compliance requirements:
B relates to resource optimization, not compliance.
C refers to interoperability, which is unrelated to regulatory auditing.
D improves security but does not directly address compliance documentation.
Refer to the exhibit.


Refer to the exhibit. An engineer must configure Cisco IOS SLB for DNS on router R1 to meet these requirements:
The first DNS request to www.ccnp.test
must be redirected to the DNS server at 10.1.1.1;
The second DNS request to www.ccnp.test
must be redirected to the DNS server at 10.2.1.1;
The third DNS request to www.ccnp.test
must be redirected to the DNS server at 10.3.1.1.
In each case, the other two addresses must also be attempted if the first one fails. The indicated configuration was applied to R1; however, the load balancing failed. Which command must be run on R1 to resolve the issue?
On R1 the configuration (simplified) is:
ip domain lookup
ip domain name ccnp.test
ip host www.ccnp.test 10.1.1.1 10.2.1.1 10.3.1.1
The ip host command statically maps the hostname www.ccnp.test
to three IP addresses. By default, Cisco IOS will always return these IP addresses to DNS queries in the same order they are configured (10.1.1.1, then 10.2.1.1, then 10.3.1.1). This means that clients will always attempt 10.1.1.1 first and will not achieve per-query load balancing across all three servers.
To enable DNS-based load balancing so that each successive query rotates the order of the addresses, Cisco IOS provides the command:
ip domain round-robin
This command enables round-robin rotation of multiple A records associated with a single hostname defined by ip host. With this feature enabled:
1st query: response order 10.1.1.1, 10.2.1.1, 10.3.1.1
2nd query: response order 10.2.1.1, 10.3.1.1, 10.1.1.1
3rd query: response order 10.3.1.1, 10.1.1.1, 10.2.1.1
Clients will typically try the first IP address in the list and use the others if the first one fails, exactly matching the requirement.
Why other options are incorrect:
A . ip domain retry 3 controls how many times the router retries DNS queries to a server; it does not control the order of multiple A records.
C . ip dns server turns the router into a DNS server but does not itself provide round-robin behavior for statically defined hosts.
D . maximum-paths 3 is a routing (IP forwarding) parameter for equal-cost multipath, unrelated to DNS resolution.