At ValidExamDumps, we consistently monitor updates to the Arcitura Education S90.20 exam questions by Arcitura Education. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Arcitura Education SOA Security Lab exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Arcitura Education in their Arcitura Education S90.20 exam. These outdated questions lead to customers failing their Arcitura Education SOA Security Lab exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Arcitura Education S90.20 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
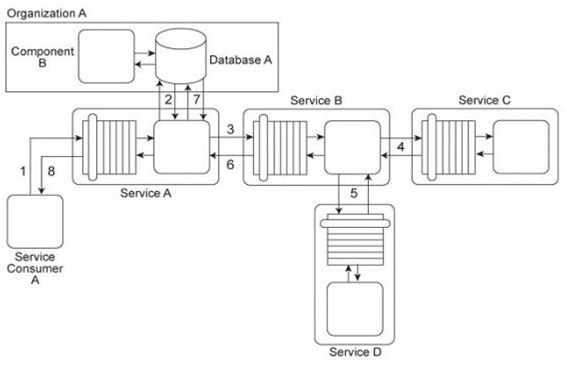
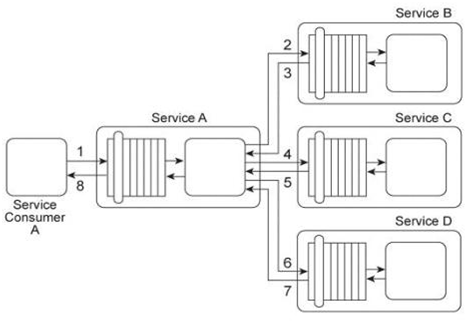
Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial data from Database A (2). Service A then sends a request message with the retrieved data to Service B (3). Service B exchanges messages with Service C (4) and Service D (5), which perform a series of calculations on the data and return the results to Service A .Service A uses these results to update Database A (7) and finally sends a response message to Service Consumer A (8). Component B has direct, independent access to Database A and is fully trusted by Database A .Both Component B and Database A reside within Organization A .Service Consumer A and Services A, B, C, and D are external to the organizational boundary of Organization A .Service A has recently experienced an increase in the number of requests from Service Consumer A .However, the owner of Service Consumer A has denied that Service Consumer A actually sent these requests. Upon further investigation it was determined that several of these disclaimed requests resulted in a strange behavior in Database A, including the retrieval of confidential data. The database product used for Database A has no feature that enables authentication of consumers. Furthermore, the external service composition (Services A, B, C, D) must continue to operate at a high level of runtime performance. How can this architecture be improved to avoid unauthenticated access to Database A while minimizing the performance impact on the external service composition?
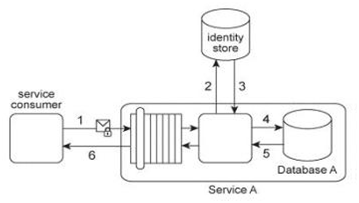
Service A provides a data access capability that can be used by a variety of service consumers. The database records accessed by Service A are classified as either private or public. There are two types of service consumers that use Service A:
Service consumers with public access permissions (allowed to access only public data records) and service consumers with private access permissions (allowed to access all data records). For performance reasons the Service A architecture uses a single database, named Database A .Each record in Database A is classified as either private or public. After Service A is invoked by a service consumer (1), it authenticates the request message using an identity store and retrieves the corresponding authorization (2, 3). Once authorized, the service consumer's request is submitted to Database A (4), which then returns the requested data (5) If the service consumer has private access permissions, all of the returned data is included in Service A's response message (6). If the service consumer has public access permissions, then Service A first filters the data in order to remove all unauthorized private data records, before sending to the response message to the service consumer (6). An investigation recently detected that private data has been leaked to unauthorized service consumers. An audit of the Service A architecture revealed that Service A's filtering logic is flawed, resulting in situations where private data was accidentally shared with service consumers that only have public access permissions. Further, it was discovered that attackers have been monitoring response messages sent by Service A in order to capture private data. It is subsequently decided to split Database A into two databases:
one containing only private data (the Private Database) and the other containing only public data (the Public Database). What additional changes are necessary to address these security problems?
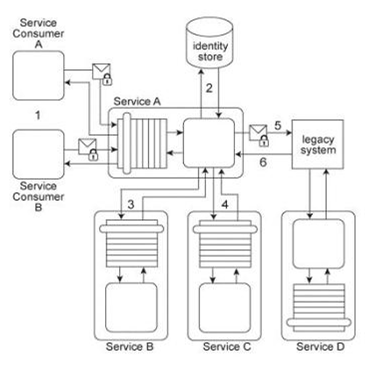
Service A has two specific service consumers, Service Consumer A and Service Consumer B (1). Both service consumers are required to provide security credentials in order for Service A to perform authentication using an identity store (2). If a service consumer's request message is successfully authenticated, Service A processes the request by exchanging messages with Service B (3) and then Service C (4). With each of these message exchanges, Service A collects data necessary to perform a query against historical data stored in a proprietary legacy system. Service A's request to the legacy system must be authenticated (5). The legacy system only provides access control using a single account. If the request from Service A is permitted, it will be able to access all of the data stored in the legacy system. If the request is not permitted, none of the data stored in the legacy system can be accessed. Upon successfully retrieving the requested data (6), Service A generates a response message that is sent back to either Service Consumer A or B .The legacy system is also used independently by Service D without requiring any authentication. Furthermore, the legacy system has no auditing feature and therefore cannot record when data access from Service A or Service D occurs. If the legacy system encounters an error when processing a request, it generates descriptive error codes. This service composition architecture needs to be upgraded in order to fulfill the following new security requirements:
1. Service Consumers A and B have different access permissions and therefore, data received from the legacy system must be filtered prior to issuing a response message to one of these two service consumers.
2. Service Consumer A's request messages must be digitally signed, whereas request messages from Service Consumer B do not need to be digitally signed. Which of the following statements describes a solution that fulfills these requirements?
Service A provides a data retrieval capability that can be used by a range of service consumers, including Service Consumer A, In order to retrieve the necessary data. Service Consumer A first sends a request message to Service A (1). Service A then exchanges request and response messages with Service B (2, 3). Service C (4, 5), and Service D (6. 7). After receiving all three response messages from Services B .C .and D, Service A assembles the collected data into a response message that it returns to Service Consumer A (8). The Service A data retrieval capability has been suffering from poor performance, which has reduced its usefulness to Service Consumer A .Upon studying the service composition architecture, it is determined that the performance problem can be partially attributed to redundant validation by service contracts for compliance to security policies. Services B and C have service contracts that contain the same two security policies. And, Service D has a service contract that contains a security policy that is also part of Service A's service contract. What changes can be made to the service contracts in order to improve the performance of the service composition while preserving the security policy compliance requirements?
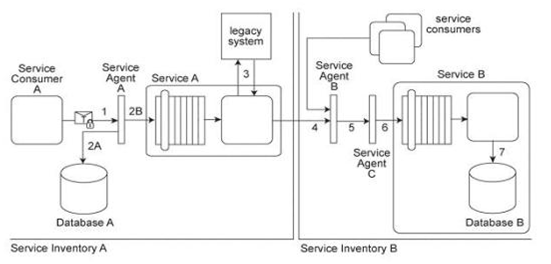
Service Consumer A sends a request message with an authentication token to Service A, but before the message reaches Service A, it is intercepted by Service Agent A (1). Service Agent A validates the security credentials and also validates whether the message is compliant with Security Policy A .If either validation fails, Service Agent A rejects the request message and writes an error log to Database A (2A). If both validations succeed, the request message is sent to Service A (2B). Service A retrieves additional data from a legacy system (3) and then submits a request message to Service B Before arriving at Service B, the request message is intercepted by Service Agent B (4) which validates its compliance with Security Policy SIB then Service Agent C (5) which validates its compliance with Security Policy B .If either of these validations fails, an error message is sent back to Service A .that then forwards it to Service Agent A so that it the error can be logged in Database A (2A). If both validations succeed, the request message is sent to Service B (6). Service B subsequently stores the data from the message in Database B (7). Service A and Service Agent A reside in Service Inventory A .Service B and Service Agents B and C reside in Service Inventory B .Security Policy SIB is used by all services that reside in Service Inventory B .Service B can also be invoked by other service from within Service Inventory B .Request messages sent by these service consumers must also be compliant with Security Policies SIB and B .New services are being planned for Service Inventory A .To accommodate service inventory-wide security requirements, a new security policy (Security Policy SIA) has been created. Compliance to Security Policy SIA will be required by all services within Service Inventory A .Some parts of Security Policy A and Security Policy SIB are redundant with Security Policy SIA .How can the Policy Centralization pattern be correctly applied to Service Inventory A without changing the message exchange requirements of the service composition?